The easiest way to learn is by practice. This is especially true in IT. I have to lab out the migration from pfSense 1.2.3 to 2.0 RC1. Furthermore I have a site-to-site VPN setup that must be tested too.
I decided to expand my laboratory setup to house not just the two versions of pfSense, but DD-WRT and OpenWrt also. This will give me a opportunity to expand my test with alternatives. That is not enough, so let’s add two of each as virtual machines. Now we need a router in the middle to move the traffic between different subnets. Using any of the above will be redundant, so after browsing the VMware market for router appliance, as first option came Untangle, but I have already played around with it, and it is not appropriate for my purposes. As reasonable alternative is Vyatta. I had no experience with this appliance, and decide to check it out.
My finale network diagram looks like this:
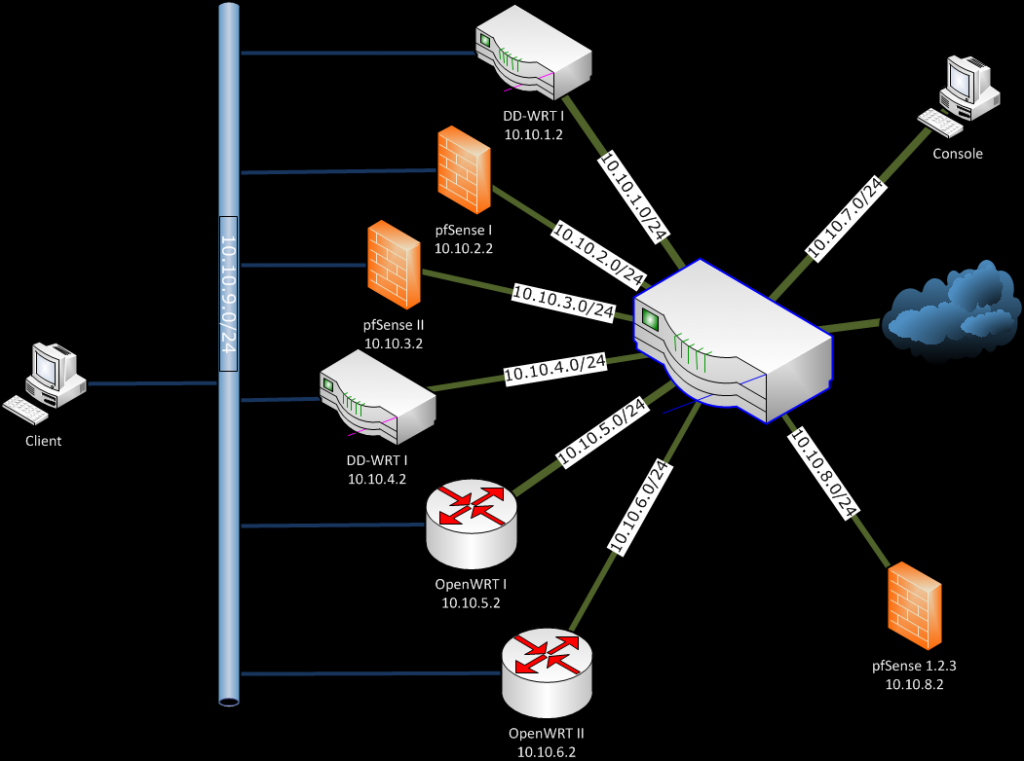
The Console and Client are a simple Windows XP workstation from which to manage all the routers remotely by SSH and Web Interface.
As you can imagine if all the routers WAN addresses were in one sub-net, the Vyatta would be unnecessary, but my decision was based on the need to be able to test load balancing, fail over, and other scenarios in future.
In the following post I will discuss in details the configuration of each type of route. As a brief impression from the installation and configuration starting from the easiest to setup and going to the hardest ones.
PfSense have a Live CD, and is a breeze to install and configure on x86 virtual machine.
Then is the Vyatta, also available on Live CD that can be installed on virtual machine. For the configuration I have used the shell, only later to discover that there is a web interface that is somewhat helpful.
DD-WRT is hard to get on x86 virtual machine. I have opt out to find ready-made virtual machine and only to restore it to default configuration, and then to configure it to my preferences.
OpenWrt is even harder. On the forums the recommended way is to compile it for this architecture, and then install it. There is a wonderful tutorial here how to set it up on virtual box, but it does not work on VMware workstation. My guess is if you reconfigure the hard disk portions it will work. But yet again, my decision was to use ready-made virtual machine with the latest version, and configure it to my likings.
The easiest way to learn is by practice. This is especially true in IT. So now I have to lab out the migration from pfSense 1.2.3 to 2.0 RC1. Furthermore I have a site-to-site VPN setup that must be tested too.
I decided to expand my laboratory setup to house not just the two versions of pfSense, but DD-WRT and OpenWrt also. That is not enough, so let’s add two of each as virtual machines. Now we need a router in the middle to move the traffic between different subnets. Using any of the above will be redundant, so after browsing the VMware market for router appliance, as first option came Untangle, but I have already played around with it, and it is not appropriate for my purposes. As alternative to Untangle, Vyatta pop up from the result. I had no experience with this appliance, and decide to check it out.
My finale network diagram is like this:
The console and Client are a simple Windows XP workstation from which to manage all the routers remotely by SSH and Web Interface.
As you can imagine if all the routers WAN addresses were in one subnet, the Vyatta would be unnecessary, but my decision was based on the need to be able to test load balancing, failover, and other scenarios in future.
In the following post I will discuss in details the configuration of each type of route. Now let’s go from the fore a brief impression from the installation and configuration starting from the easiest to setup and going to the hardest ones.
PfSense have a live cd, and is a breeze to install and configure on x86 virtual machine. The only interesting this here is how to publish the web interface and the SSH on the WAN.
Then is the Vyatta, also available on live cd that can be installed on virtual machine. For the configuration I have used the shell, only later to discover that there is a web interface that is somewhat helpful.
DD-WRT is hard to get on x86 virtual machine. I have opt out to find ready-made virtual machine and only to restore it to default configuration, and then to configure it to my preferences.
The easiest way to learn is by practice. This is especially true in IT. I have to lab out the migration from pfSense 1.2.3 to 2.0 RC1. Furthermore I have a site-to-site VPN setup that must be tested too.
I decided to expand my laboratory setup to house not just the two versions of pfSense, but DD-WRT and OpenWrt also. This will give me a opportunity to expand my test with alternatives. That is not enough, so let’s add two of each as virtual machines. Now we need a router in the middle to move the traffic between different subnets. Using any of the above will be redundant, so after browsing the VMware market for router appliance, as first option came Untangle, but I have already played around with it, and it is not appropriate for my purposes. As reasonable alternative is Vyatta. I had no experience with this appliance, and decide to check it out.
My finale network diagram looks like this:
The Console and Client are a simple Windows XP workstation from which to manage all the routers remotely by SSH and Web Interface.
As you can imagine if all the routers WAN addresses were in one subnet, the Vyatta would be unnecessary, but my decision was based on the need to be able to test load balancing, failover, and other scenarios in future.
In the following post I will discuss in details the configuration of each type of route. As a brief impression from the installation and configuration starting from the easiest to setup and going to the hardest ones.
PfSense have a live cd, and is a breeze to install and configure on x86 virtual machine.
Then is the Vyatta, also available on live cd that can be installed on virtual machine. For the configuration I have used the shell, only later to discover that there is a web interface that is somewhat helpful.
DD-WRT is hard to get on x86 virtual machine. I have opt out to find ready-made virtual machine and only to restore it to default configuration, and then to configure it to my preferences.
OpenWrt is even harder. On the forums the recommended way is to compile it for this architecture, and then install it. There is a wonderful tutorial here how to set it up on virtual box, but it does not work on VMware workstation. My guess is if you reconfigure the hard disk portions it will work. But yet again, my decision was to use ready-made virtual machine with the latest version, and configure it to my likings.
OpenWrt is even harder. On the forums the recommended way is to compile it for this architecture, and then install it. There is a wonderful tutorial here how to set it up on virtual box, but it does not work on VMware workstation. My guess is if you reconfigure the hard disk portions it will work. But yet again, my decision was to use ready-made virtual machine with the latest version, and configure it to my likings.