If you publish sites to the Internet behind pfSense device, and then try to open the Internet address you will receive the following error message:
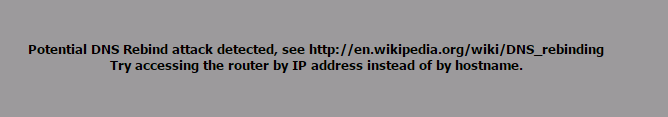
Potential DNS Rebind attack detected, see http://en.wikipedia.org/wiki/DNS_rebinding
Try accessing the router by IP address instead of by hostname.
This will appear on your browser.
Recently I’ve hit this issue.
The workaround the problem that I’ve found is as follows.
You set for the network behind the pfSense device a static DNS record for the site, pointing to the internal IP address. In this way you bypass the security checks.
The solution is as follows:
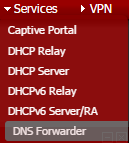
Go you the Web GUI of the pfSense, select
Services > DNS Forwarder
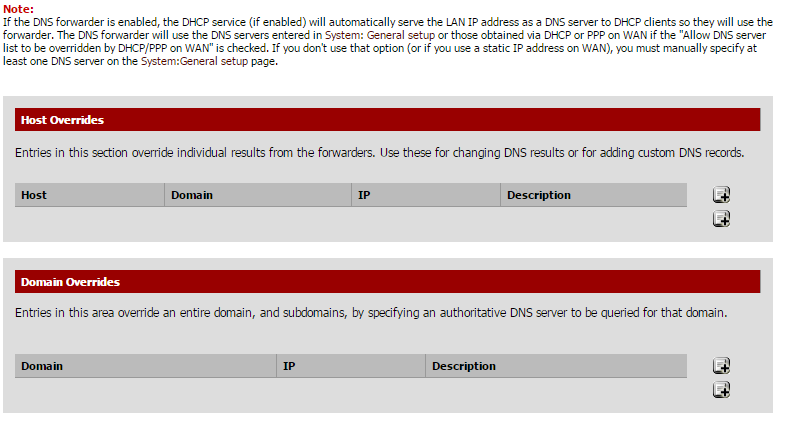
There at the bottom of the page, is the section Host Overrides.
Clock on the “+” sign in this section
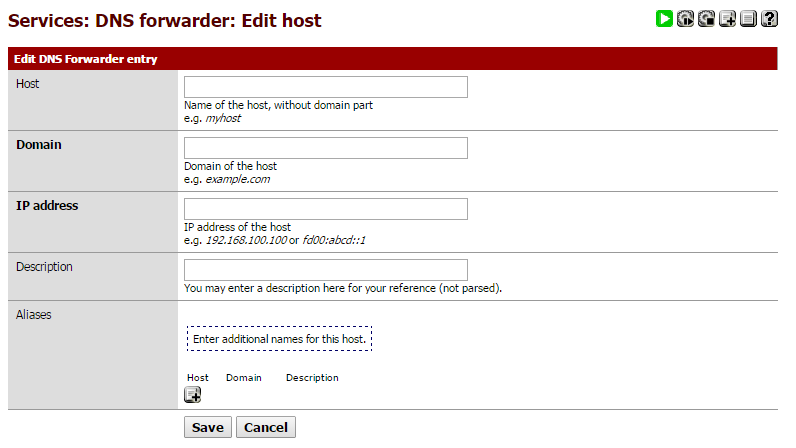
Here for the site that you want to open fill in the following:
Let’s say for example you published the site:
Something.anything.com
In the Host field enter: Something
In the Domain field enter: anything.com
In the IP Address field: enter the internal IP address of the server hosting the site
In the Description: fill something useful, so half a year later, you can remind yourself that this exception was for 😉
Click on Save.