OpenVPN 2 Cookbook
100 simple and incredibly effective recipes for harnessing the power of the OpenVPN 2 network
By Jan Just Keijser
Introduction
I was approached by Packt Publishing representative, asking if I would be willing to make a review of this book. This was interesting because at that moment I was reading pfSense 2.0 Cookbook from the same publishing company. I was generously provided with the book, and here we are a month later.
The OpenVPN 2 Cookbook main subject is the use of OpenVPN in different scenarios. Its aim is to help you along the way of implementing an OpenVPN solution. For more detail description take a look at the detailed description Here.
My experience with OpenVPN is based on three years of different deployments. You can find more details at the bottom of this post.
What’s the book about?
The book is an in depth examination of OpenVPN and how to use is in your every work. If you are in a hurry you can find a quick fix in the huge amount of recipes, or read it from cover to cover and get extensive knowledge of OpenVPN, its capabilities and different usage scenarios.
The book states that prior knowledge and experience of system administration, TCP/IP is required, also in OpenVPN installation. The examples in the book are made mostly on Linux based systems, so prior knowledge in the field is required too. If you are fresh to field, probably first step is to take a look at Beginning OpenVPN 2.0.9 and then continue with this book.
As the cover states: Quick answers to common problems.
The book is structured in twelve chapters, and each chapter consists of about eight to ten sub topics that are called recipes. These recipes are like short How Tos for a particular case. The valuable thing is that throughout the chapter the recipes build on each other, starting from very basic configuration to more advanced ones. To get an impression you can take a look at the Table of Contents.
Every recipe has a How it works sections. They are extremely useful to understand what and how is happening behind the scenes. And that’s not all, after this section additional value is provided in the There’s more sections, where additional explanations and further developments are delivered.
Does it achieve its promises?
The first topic that really gets me going was 3-way routing in the first chapter. I was planning to implement this for small number of fixed endpoints which are less than four. For more you have to read further in the book.
The next this that surprise me pleasantly was the PKI, Certificates and OpenSSL chapter. It helped me better understand OpenSSL and give me better idea how to manage certificates. This topic continues in the next chapters about Two-factor Authentication. I was very surprised to see that even hardware tokens can be used to authenticate users.
In The Scripting and Plugins, there is a very important secret about scripts execution, which was not known to me, and definitely will help me in future.
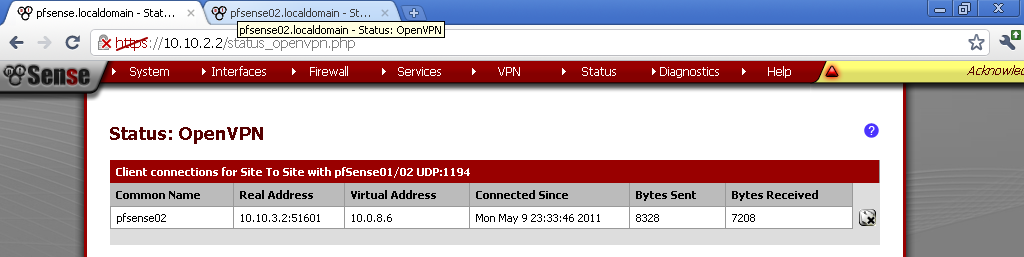
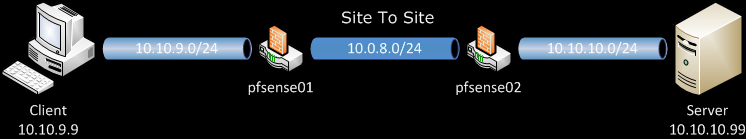
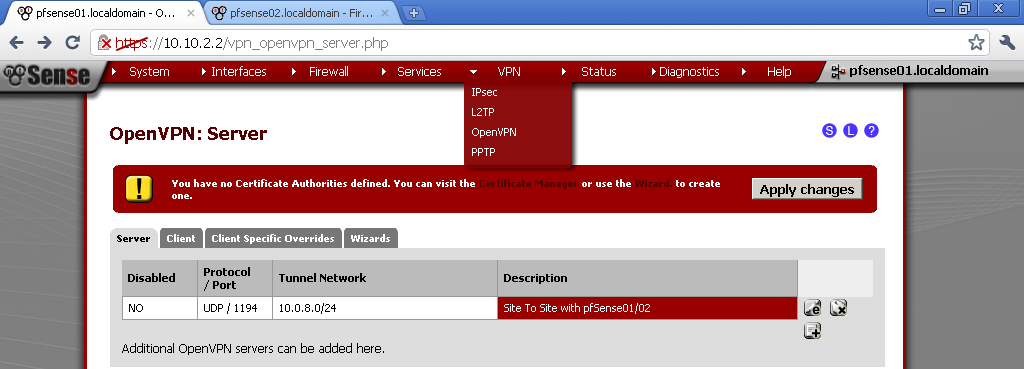
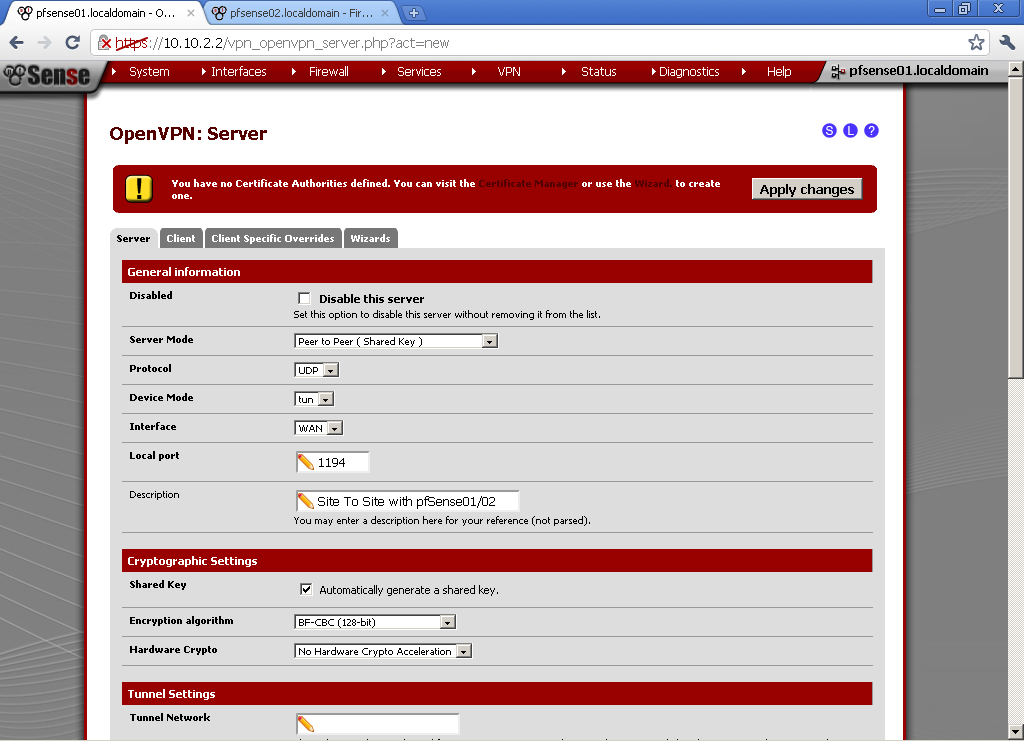
The Troubleshooting sections can save you precious blood, sweat and tears especially with problems related to Routing. Those are the two chapters I appreciate the most because they provide you with analytical way to diagnose and eliminate problems in deployments. You can have a peek in the sample chapter here: Troubleshooting OpenVPN: Configurations
Logically after you have fixed all the problems a Performance Tuning is your next step.
The following two chapters are related to OS integrations and advanced configuration. They help me better understand how to better integrate OpenVPN with the unique environment of the client.
The last chapter is all about the new features in 2.2 version of OpenVPN. It is quite useful to have a well arranged section with new features that you might have not known existed up until now.
Conclusion
I really like reading this book, and the systematic knowledge that it provides. Whether you are a full time System Administrator or just a part time occupied with the IT in your company, or just wants to establish a secure connection to your home this book will definitely give you the needed advices how to get there.
Biography
My experience with OpenVPN is based on three years’ of deployments. My first deployment was on OpenWRT where I had to use predominantly command line to configure it and Secure copy (SCP) for certificate transfer, then on DD-WRT where most of the work is done through the Web GUI, with exemption for more advanced configuration that have to be placed in start-up scripts. After that on I used Windows based systems as clients and servers, and lately as you can see from my blog I’m working with pfSense.