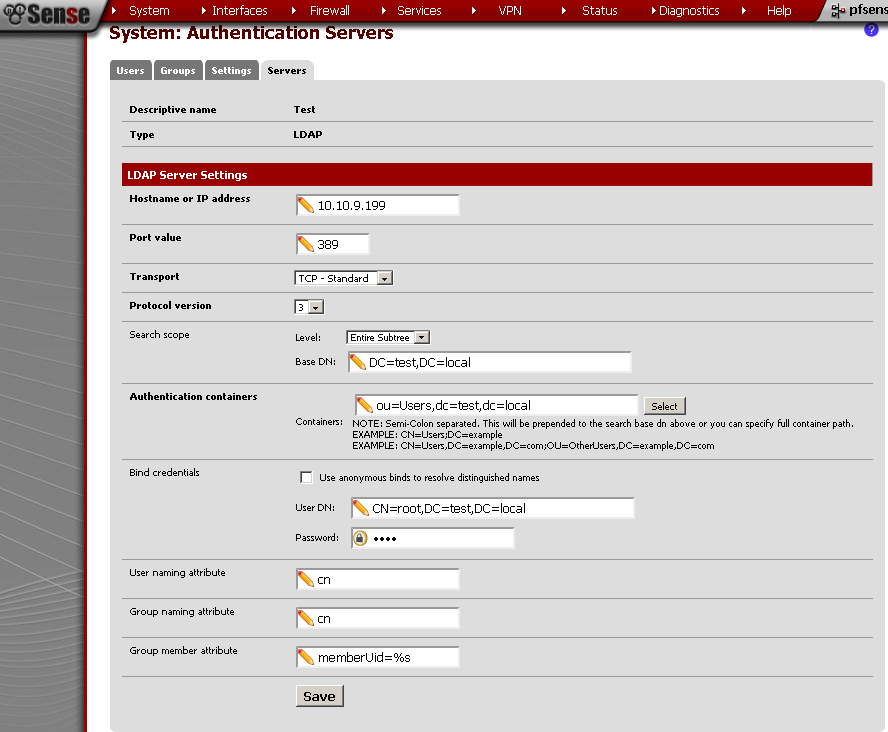
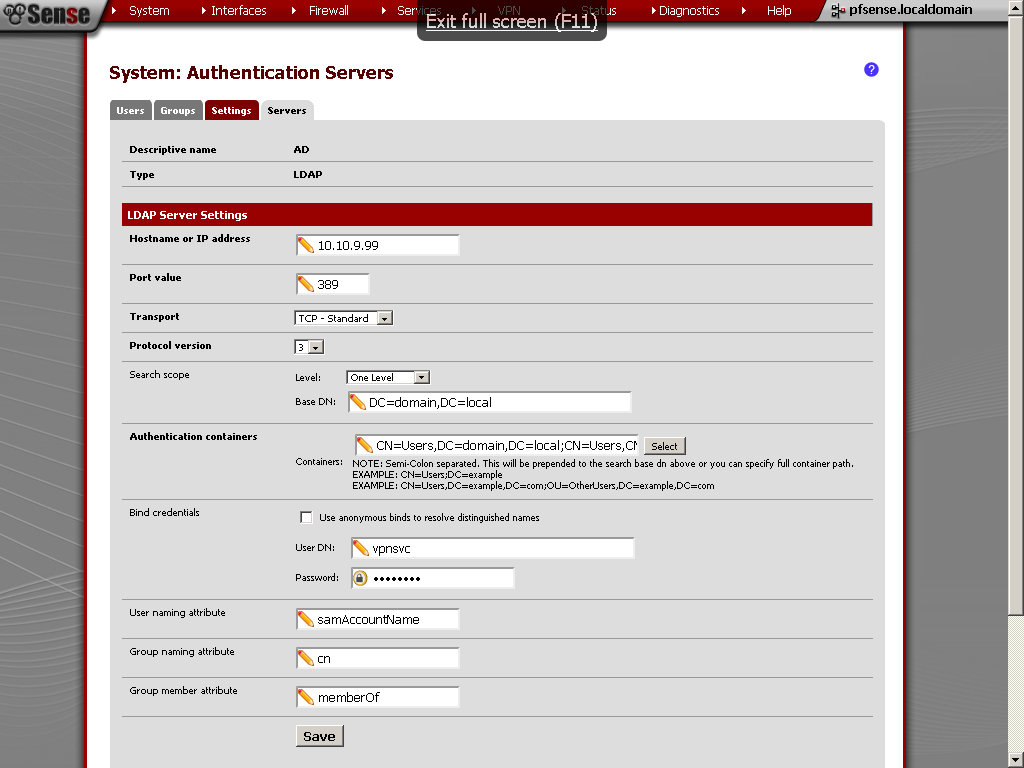
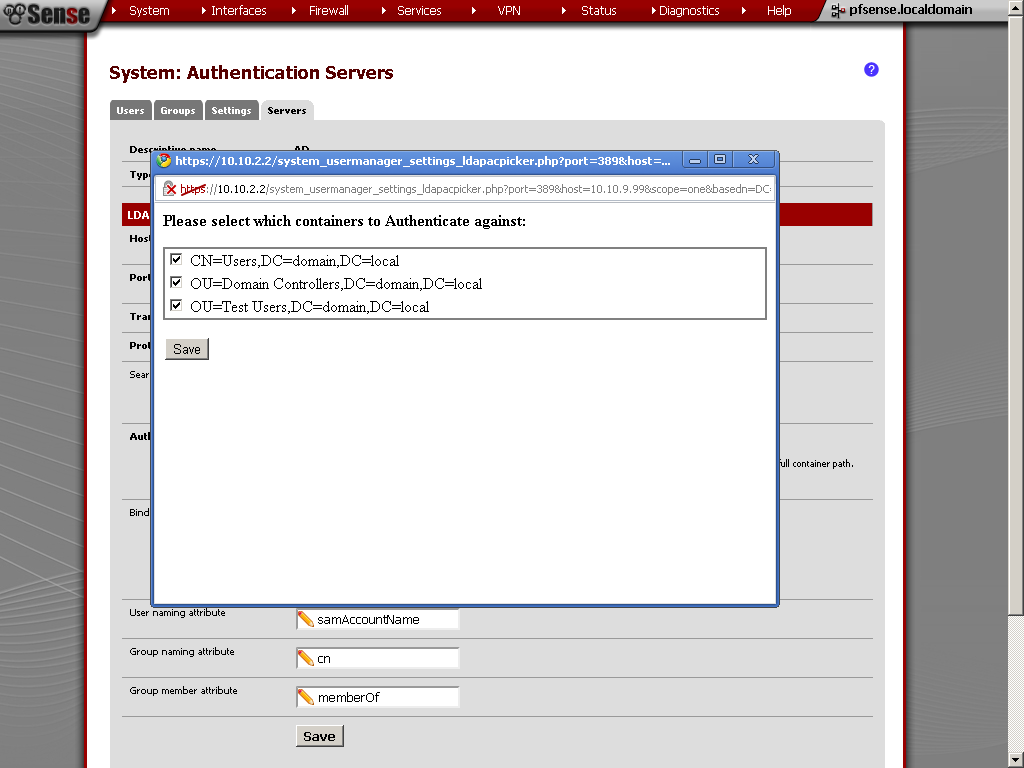
In the last post we’ve setup a Site To Site with Shared Key, now instead we will use internal Certificate Authority. Honestly speaking if I did not follow this guide, there was no routing between the two sites.
OpenVPN Site-to-Site PKI (SSL)
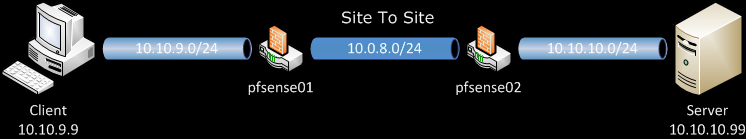
For reference here is the network diagram:
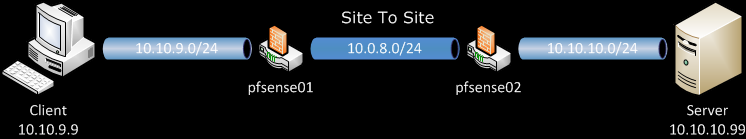
pfsense01 will be out OpenVPN server, and pfsense02 will be our OpenVPN client. Client and Server are just host on the two LANs behind routers.
On pfsense01 go to System > Cert Manager, On CAs leaf create new Certificate Authority.
Enter Descriptive Name, choose as a method Create an internal Certificate Authority, leave Key length and Lifetime to defaults.
Fill in the rest of the fields.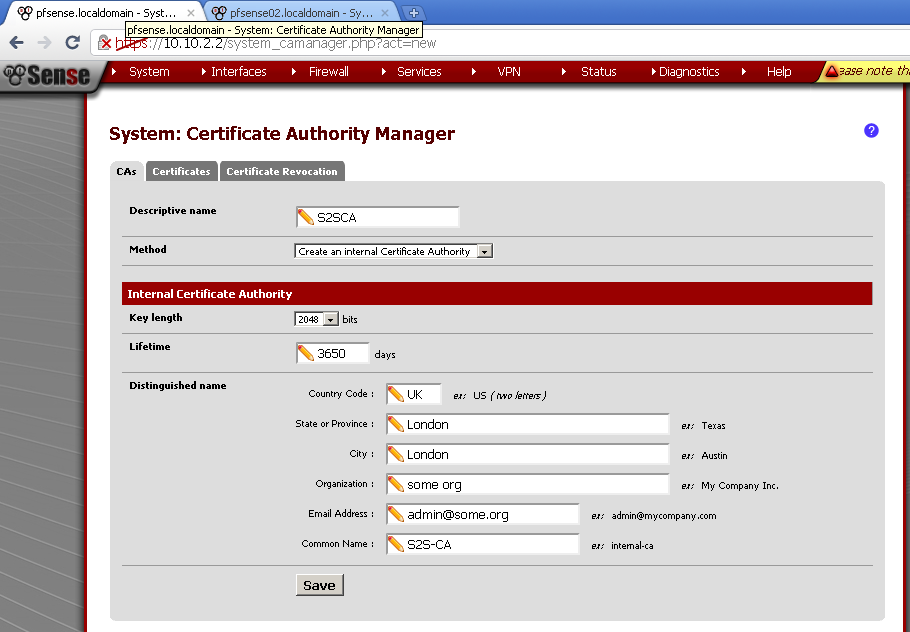
Then go to Certificates leaf, add new and create the server certificate.
Enter descriptive name, I’ve used the router host name, as a method choose Create an internal Certificate.
Verify that for Certificate authority the CA that we have created in the previous step is selected. Leave the rest of the fields to default, with exception of Common Name, here enter the host name of the server, in my case it was pfsense01.
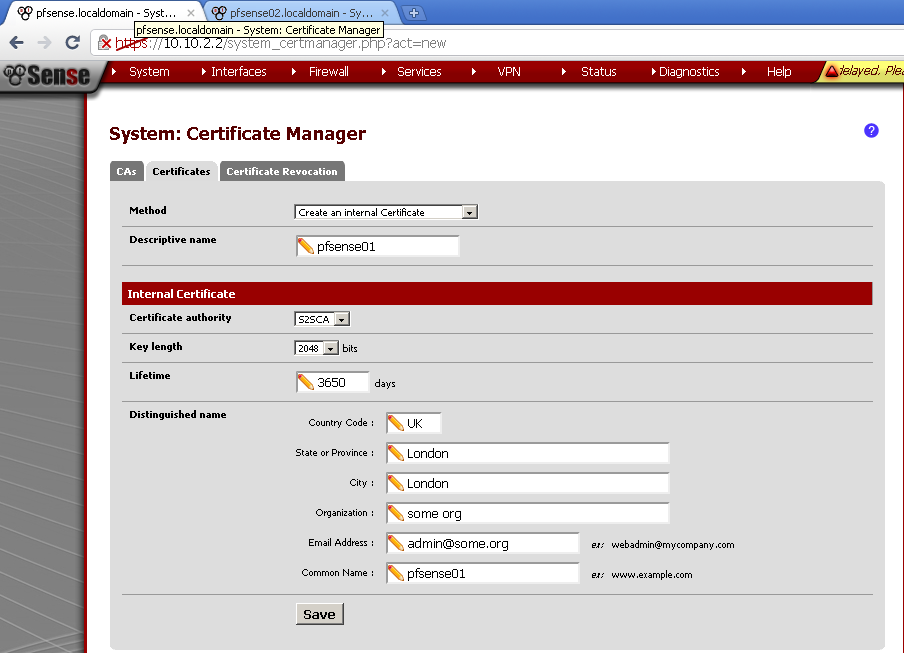
Now go to System > User manager, create new user. For the sake of simplicity for username I’ve used the host name of the second router, pfsense02. Enter Password, for Full name I’ve used again the router name. Then tick the Click to create a user certificate.
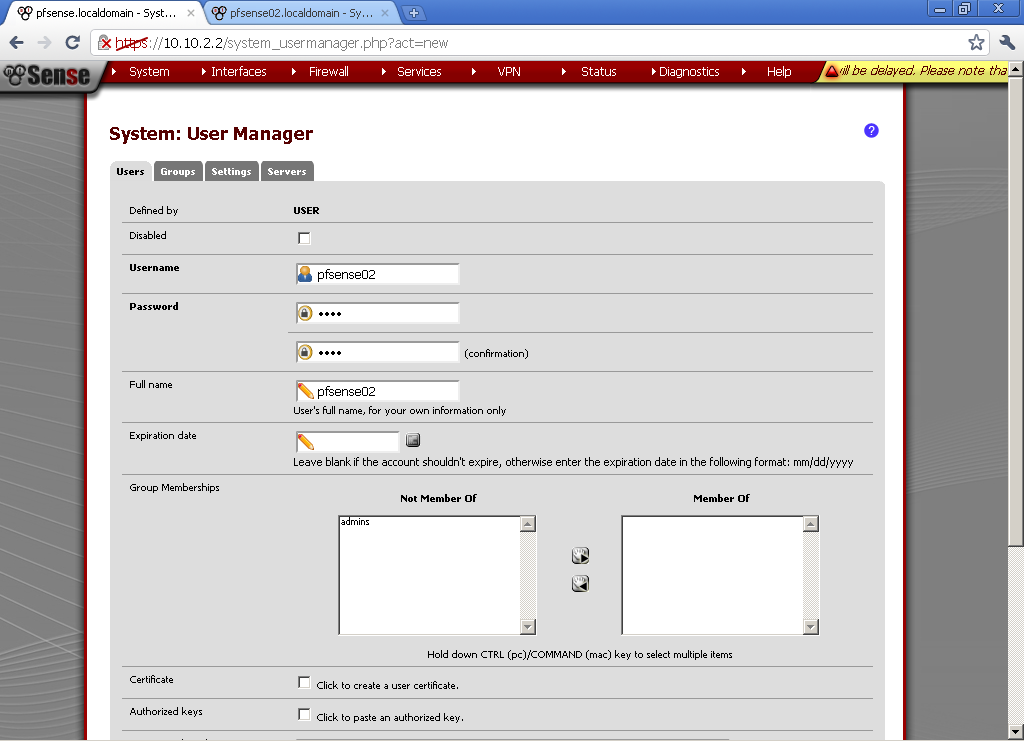
For descriptive name use the host name of the router, this is the Common Name of the certificate and it is important to match.
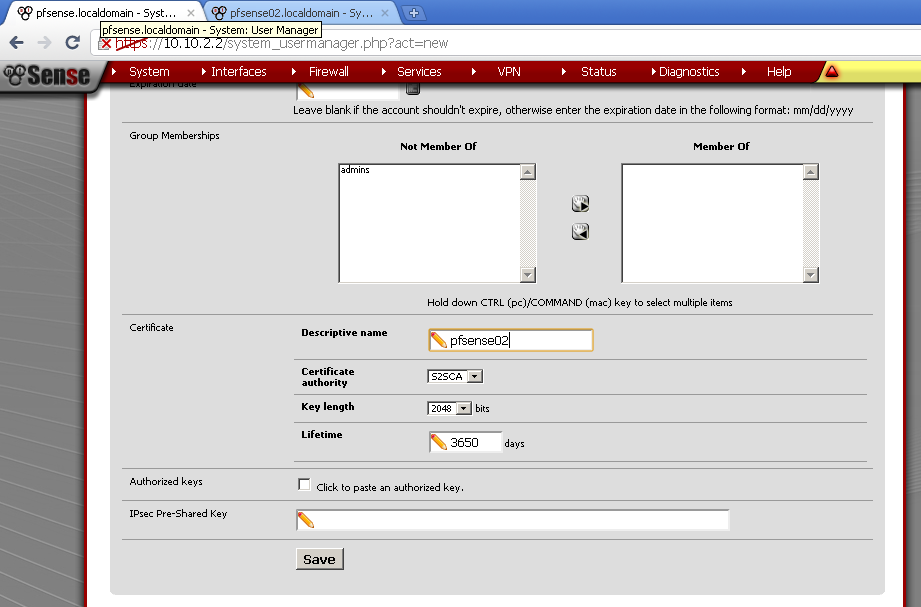
Instead of creating new user, you can create new Certificate directly.
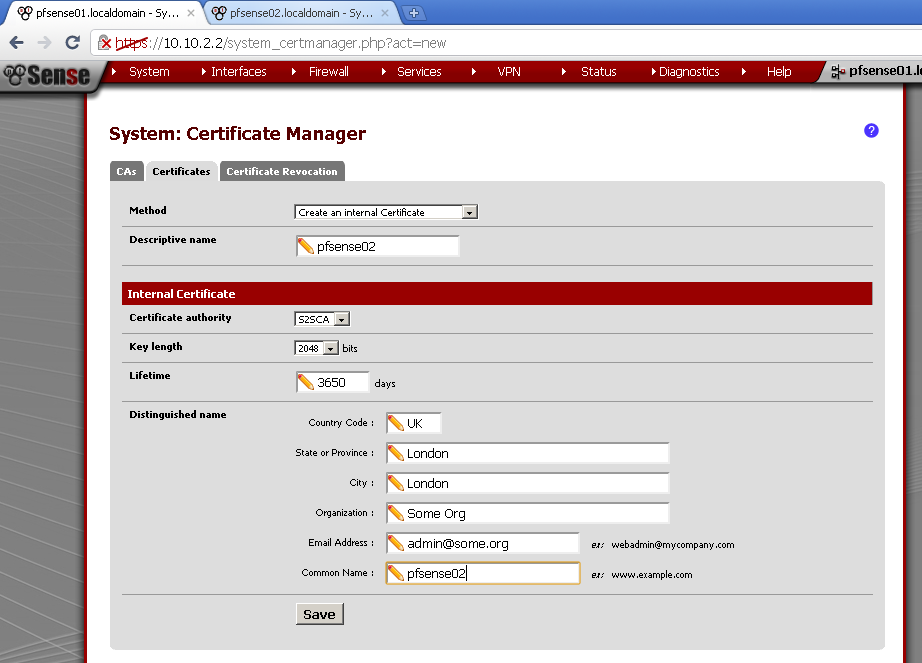
Go to Cert Manager, on the Certificate leaf add new. Again as Descriptive name and Common Name use the host name of the second router, in my case pfsense02.
Go to VPN > OpenVPN on the Server leaf, add new.
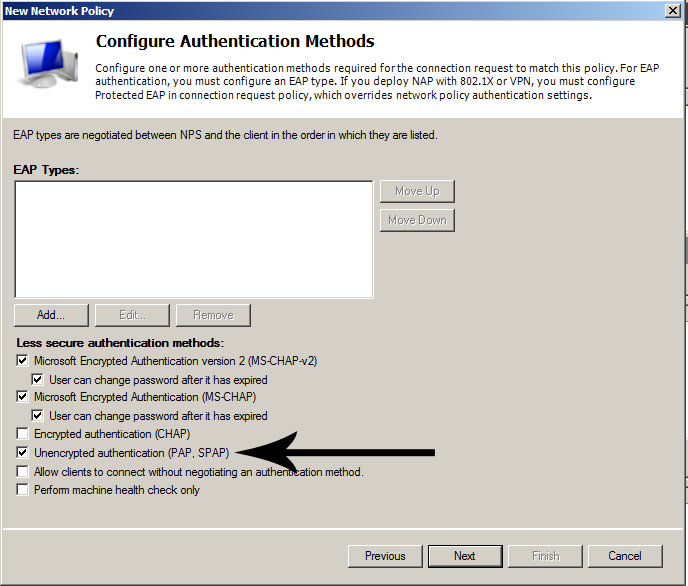
As Server Mode select Peer to Peer (SSL/TLS). As protocol UDP, Device Mode is TUN, Interface is WAN, leave the port to default 1194. Enter Description, Tick Enable authentication of TLS packets and Automatic generation a shared TLS authentication key.
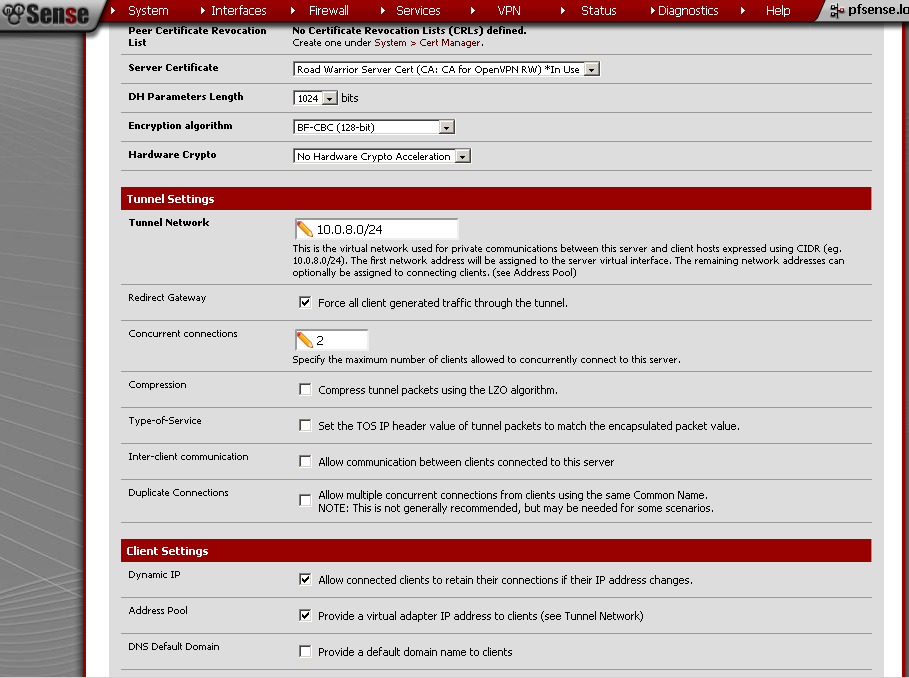
As Peer Certificate Authority select the CA that we have created in the beginning. I did not have a Peer Certification Revocation List so leave it to None. Select the Server Certificate that we have created. For DH Parameters Length you can leave it to the default 1024 bits. Choose Encryption algorithm in my case BF-CBC (128-bit), take note of the algorithm we have to use the same on the client too.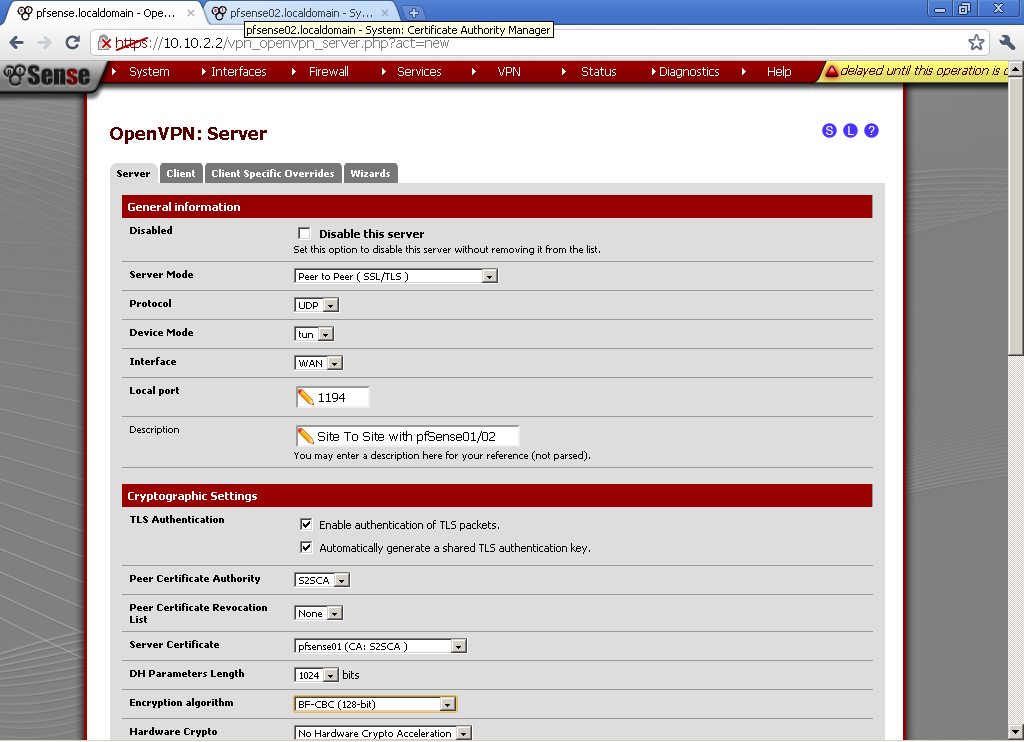
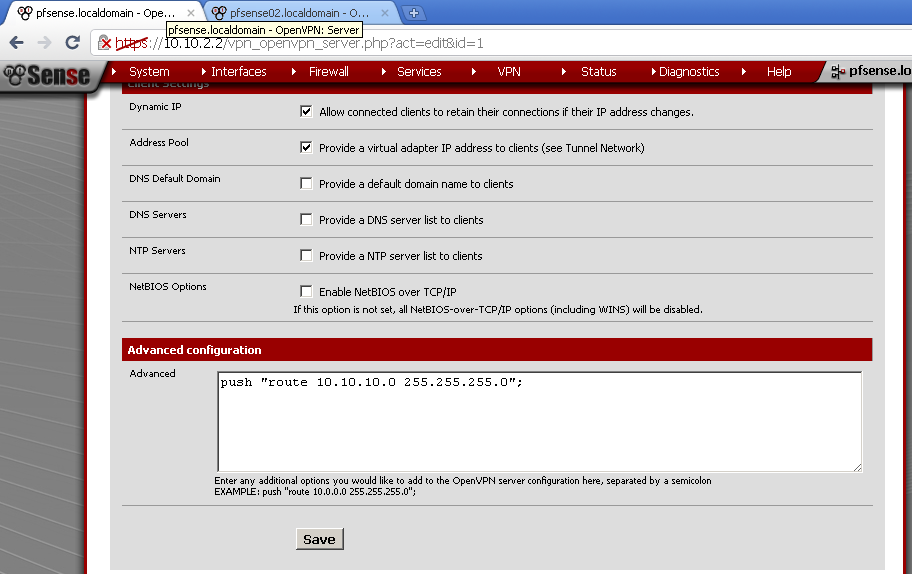
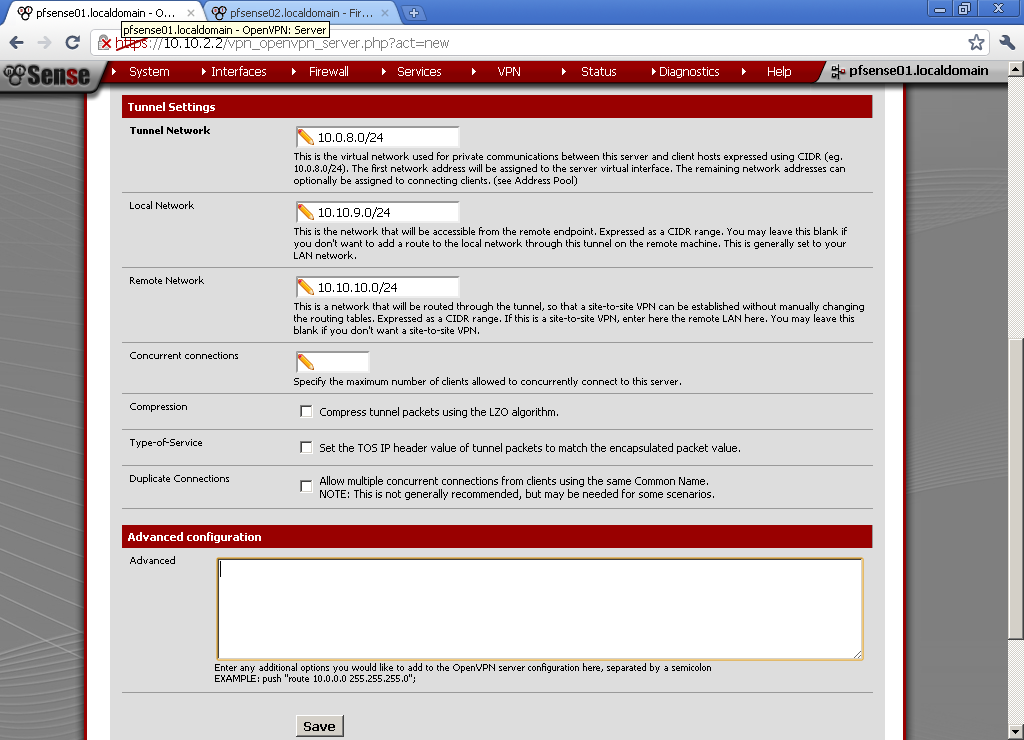
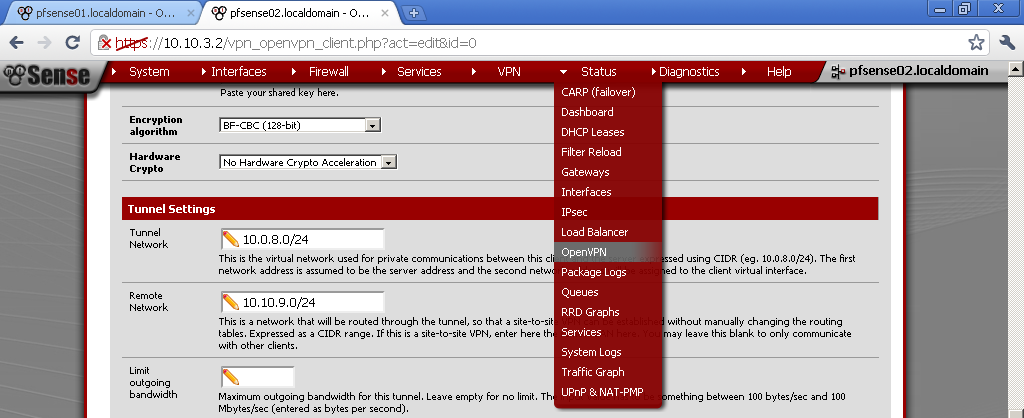
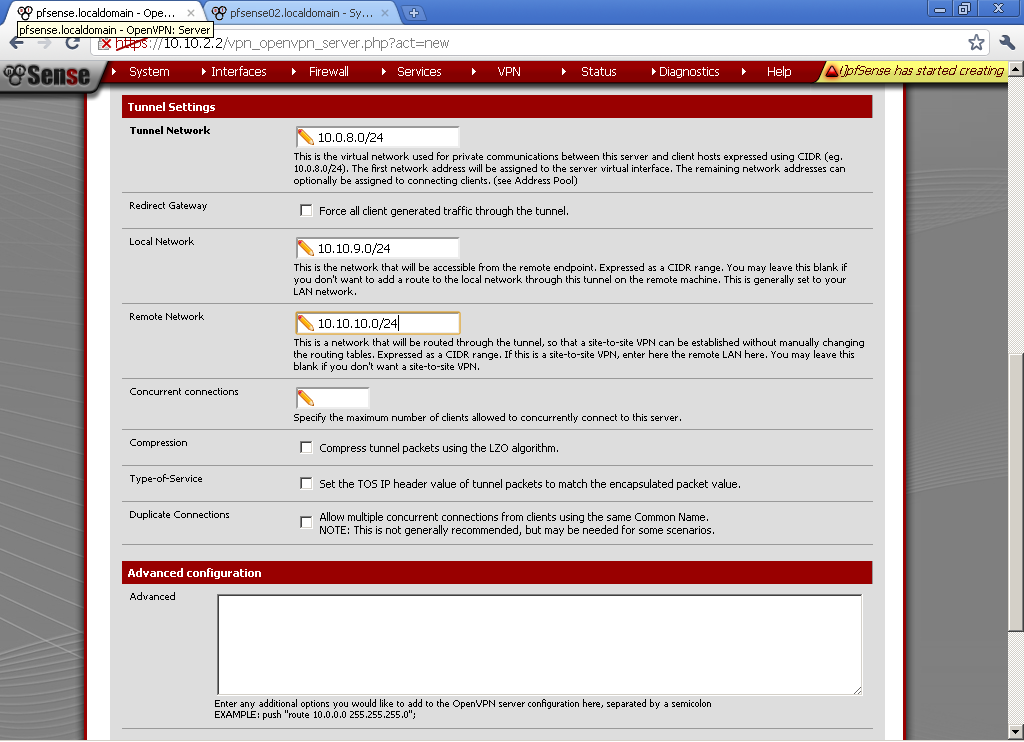
As Tunnel Network choose one different from your LANs, in my case the default 10.0.8.0/24. Enter the Local Network, in my case 10.10.9.0/24. Enter the Remote Network in my case 10.10.10.0/24. Leave the rest to defaults.
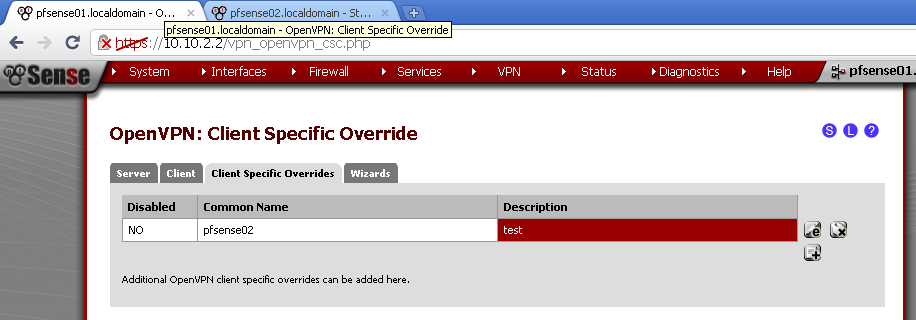
Go to VPN > OpenVPN in Client Specific Overrides, and add new entry for the client.
For Common name enter the host name of the second router that we have used as common name in the certificate, in my case pfsense02. Enter some description, and the Tunnel Network, in my case 10.0.8.0/24. Leave the rest to default.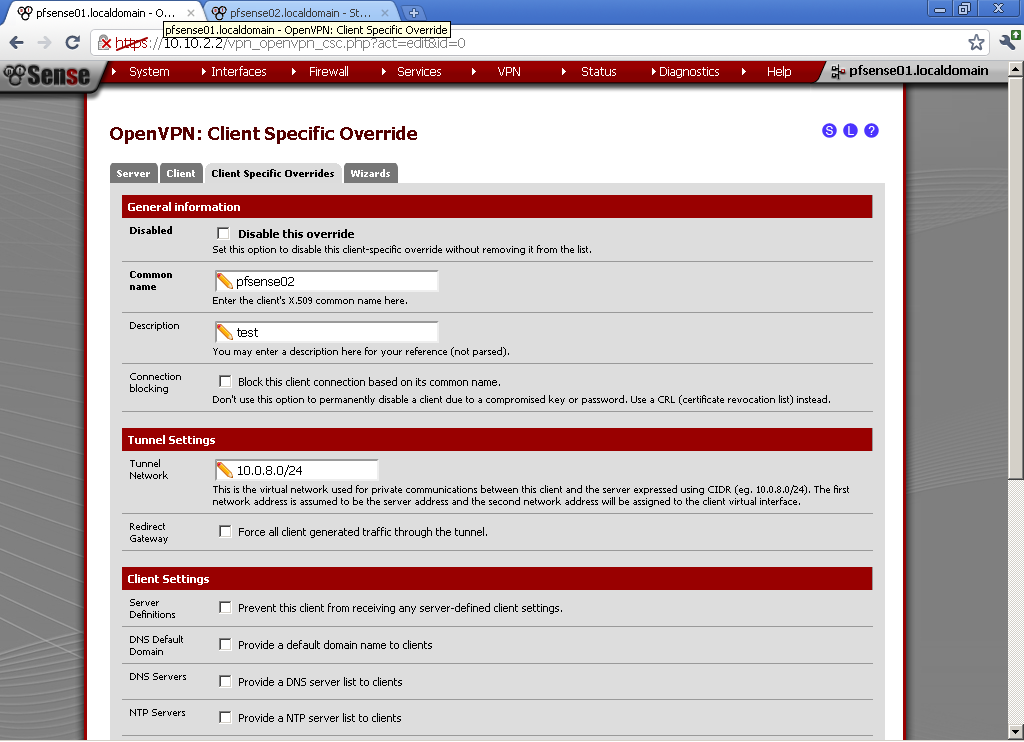
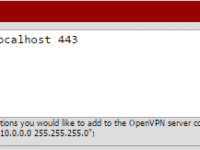
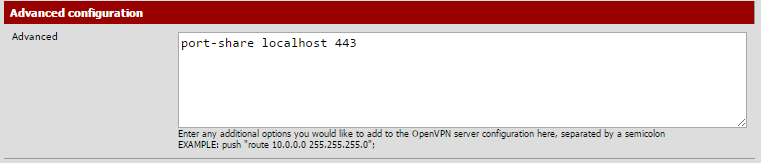
In the Advanced form, enter
iroute 10.10.10.0 255.255.255.0
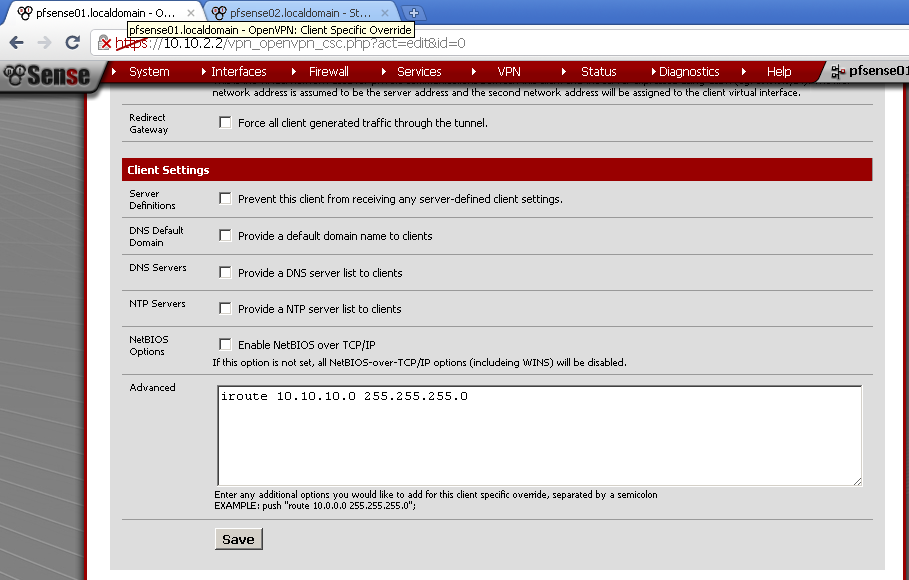 Without this step there will be no routing between the two LANs.
Without this step there will be no routing between the two LANs.
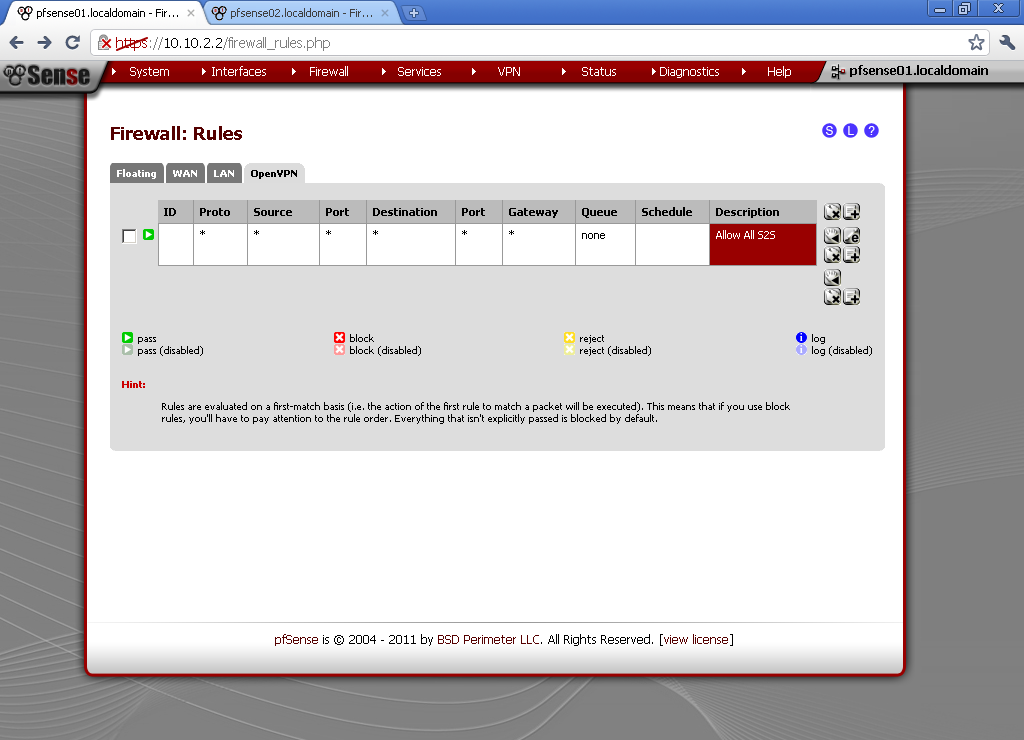
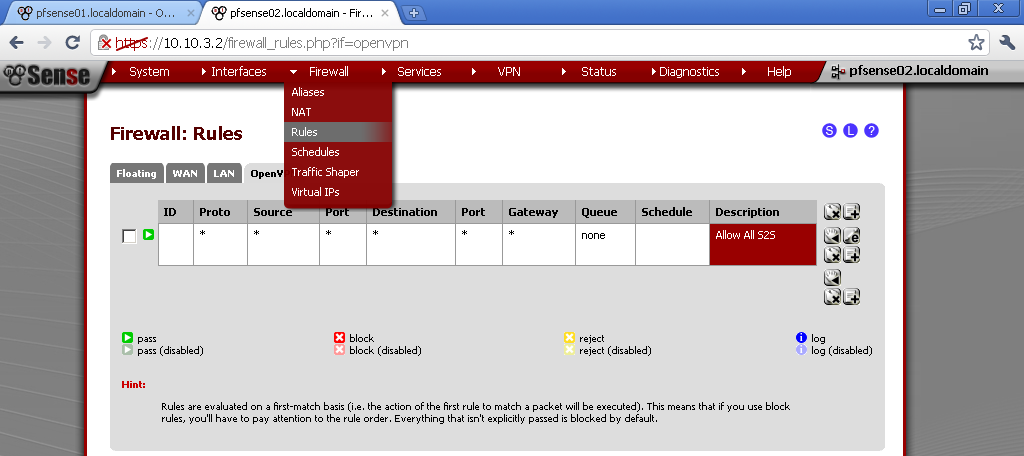
Got to Firewall >Rules and on the OpenVPN leaf, add new rule.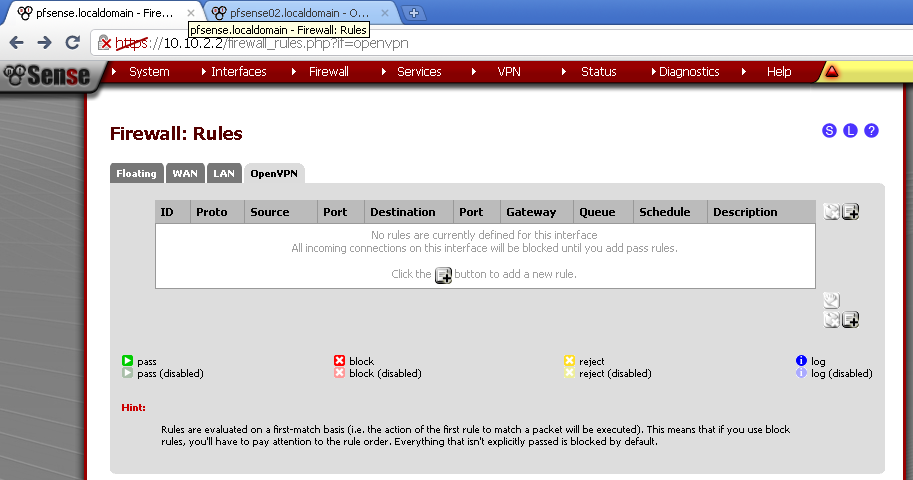
Here for testing purposes I’ve made allow all rule. Select any as Protocol, leave the rest to default and enter description.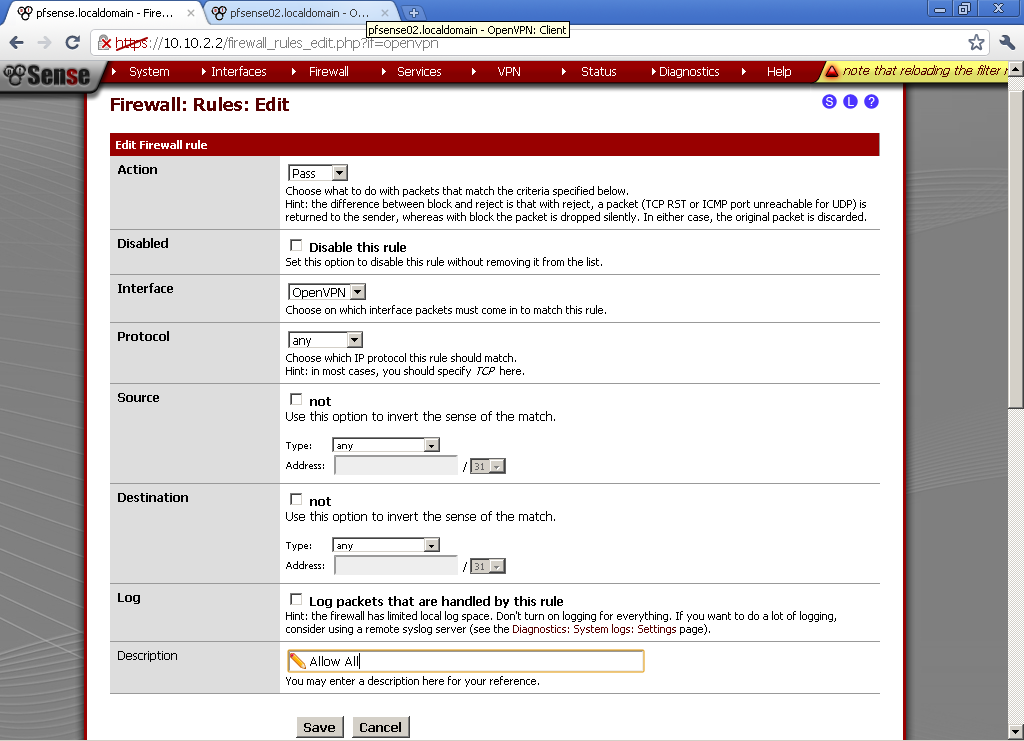
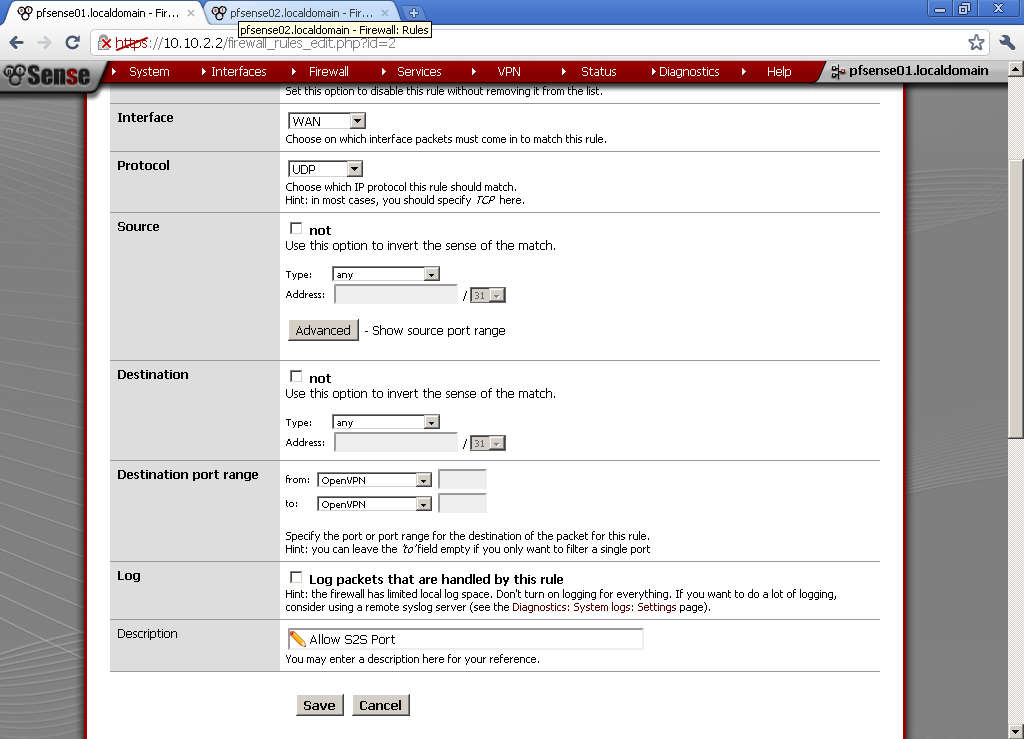
For the client to be able to connect, let’s open the OpenVPN Server port.
In Firewall > Rules on the WAN leaf, add new rule. Select UDP as Protocol.
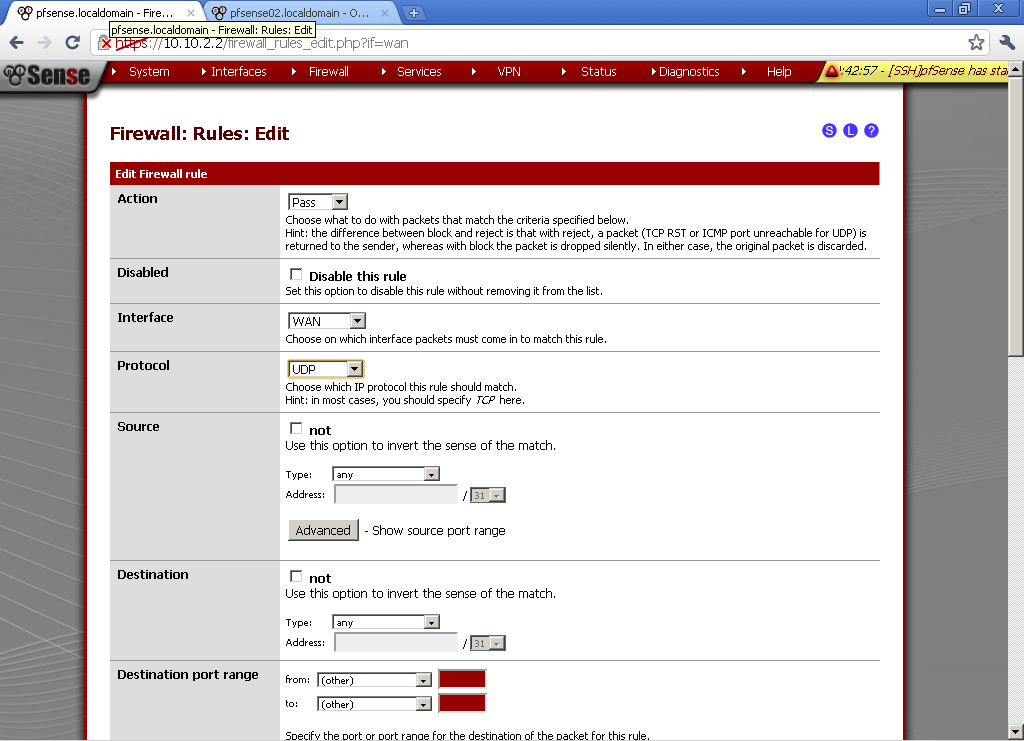
As Destination port Range in our case select OpenVPN.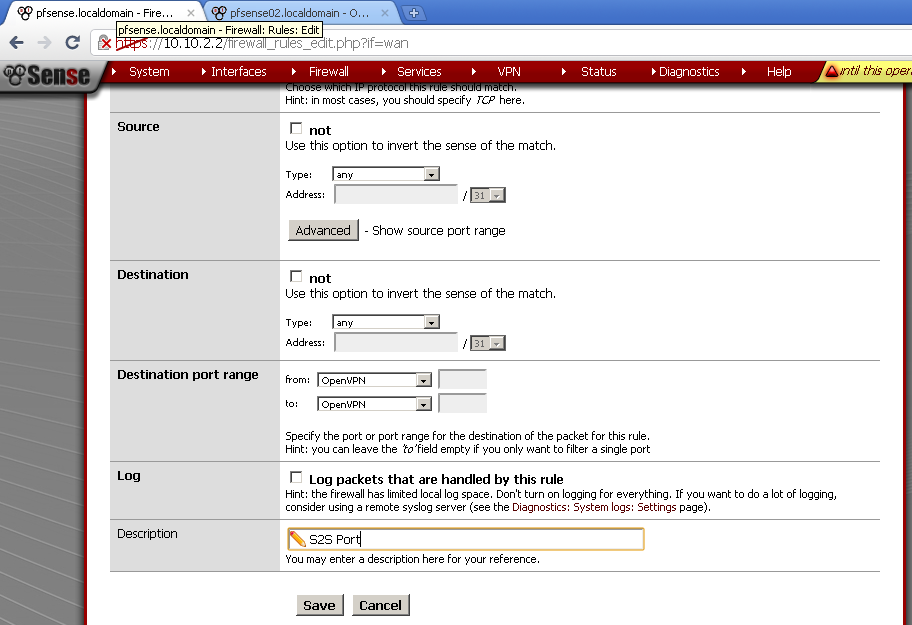
Now it is time to export certificate for use on the second router.
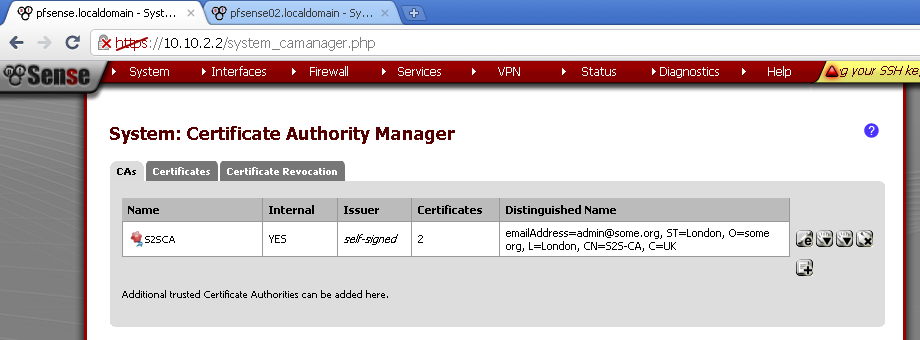
Go back to System > Cert manager export public and private CA certs, click on the first downward pointing triangle. As a guide, when you hoover over it the text label is Export CA.
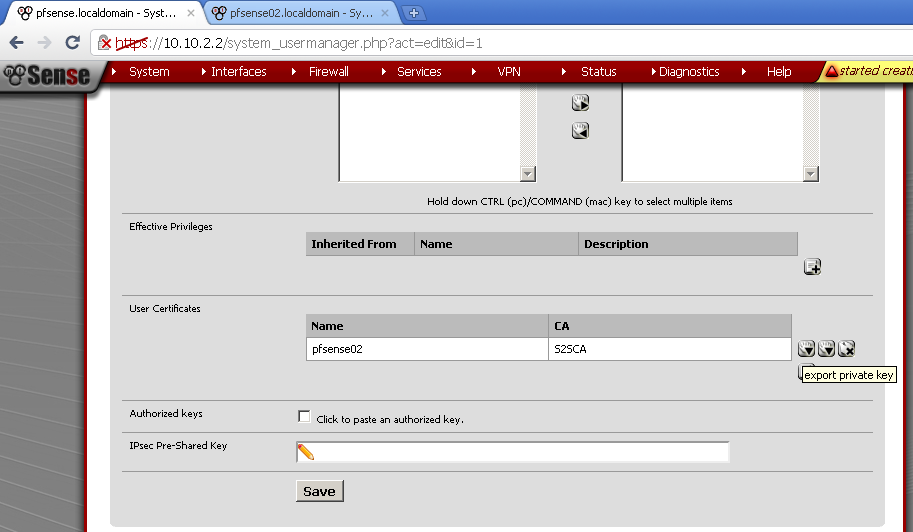
Then go to User Manager, enter the configuration of our user pfsense02, in the User Certificates section click on both downward pointing triangles to download both cert and key.
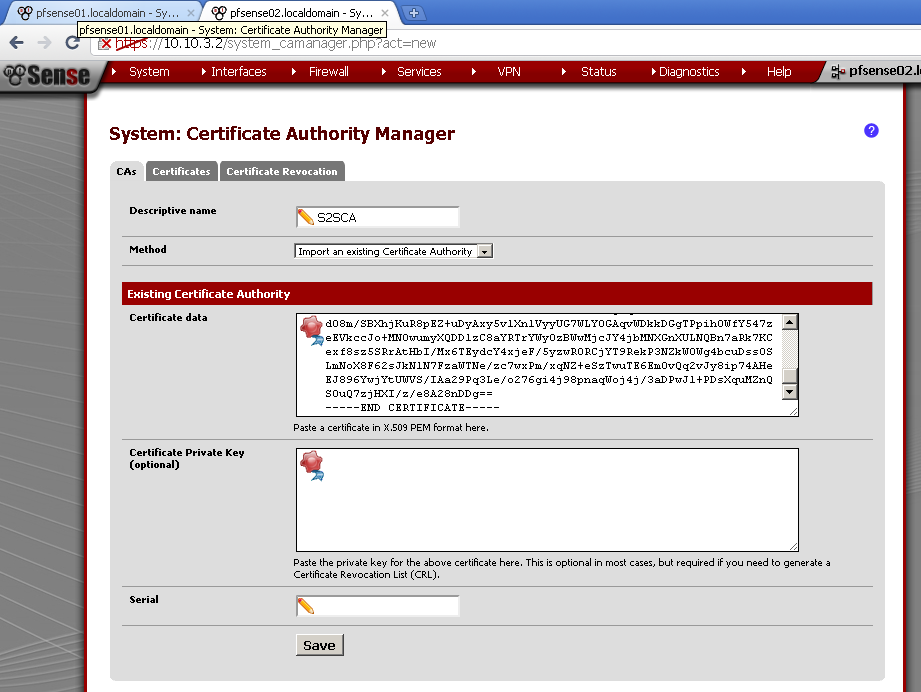
Now on pfSense02, go to System > Cert Manager on CAs leaf, add new one.
And as Method select Import an existing Certificate Authority. Enter as Descriptive name the name of the certificate from the first server, in my case pfsense01.
You have to have opened the certificate with notepad, or another text editor. Then simply copy / paste the content of the file.
Now on the Certificate leaf do the same but paste and the content of the *.key in Private key data. Again enter Descriptive name as the one from the first router.
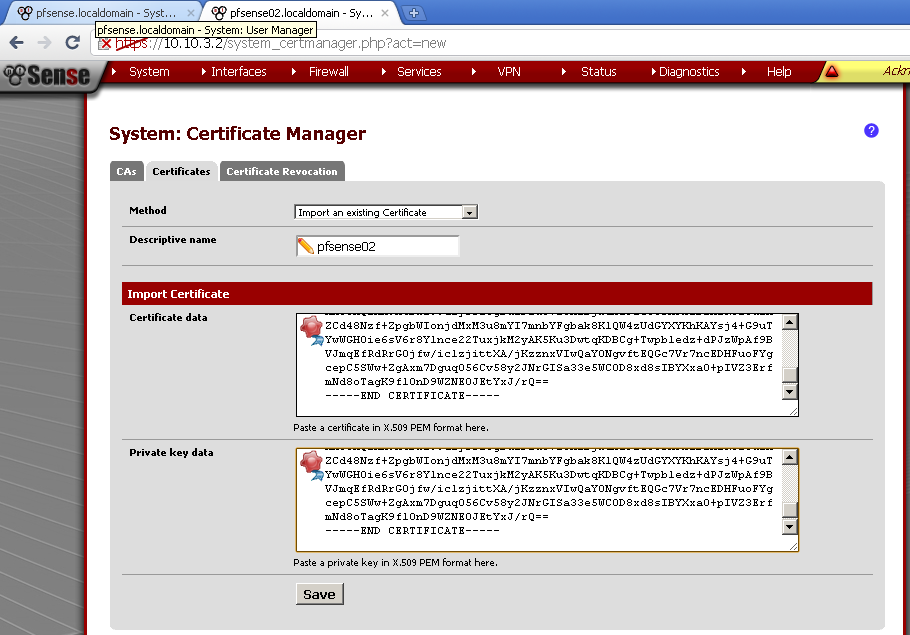
Go to VPN > OpenVPN in Client leaf and add new
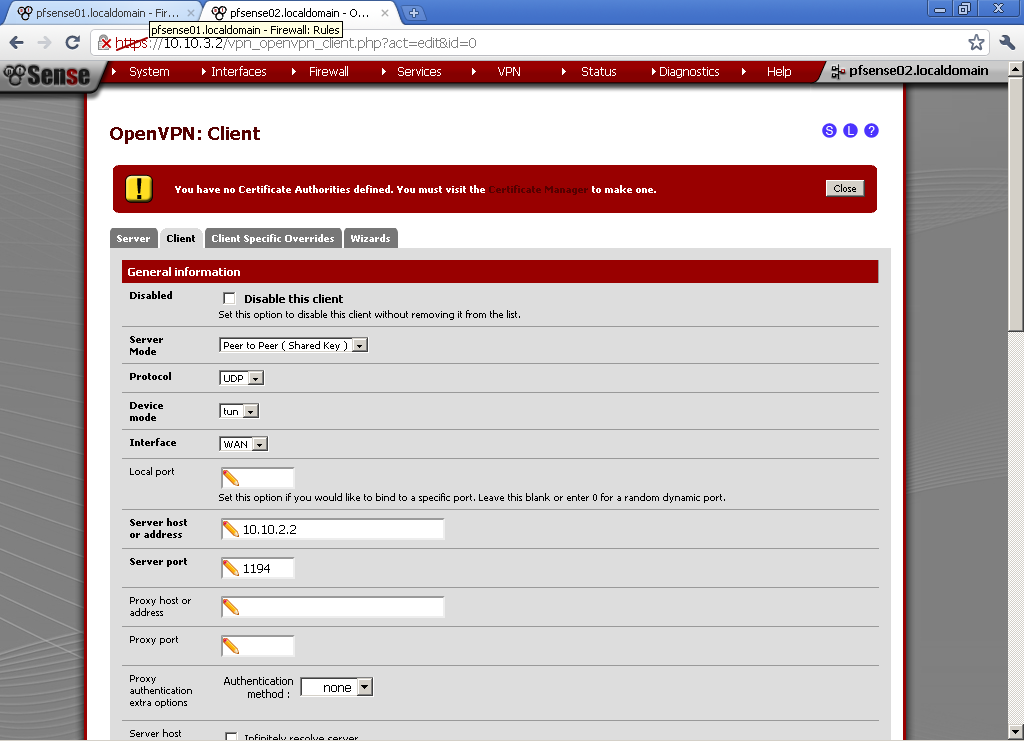
As Server Mode select Peer to Peer (SSL/TLS), Protocol is UDP, Device mode is TUN, and Interface is WAN. For Server host or address enter the WAN IP of pfsense01, in my case 10.10.2.2 and enter the port. Put some Description.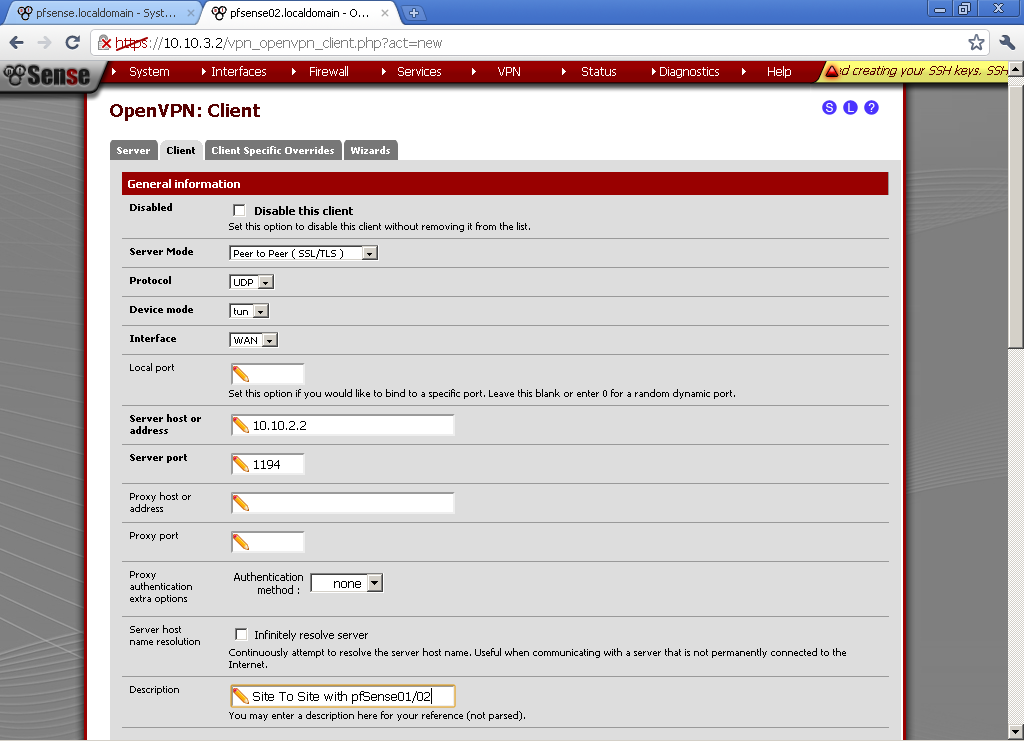
Open the Server configuration (VPN > OpenVPN > Server leaf) on pfsense01, copy the TLS Authentication.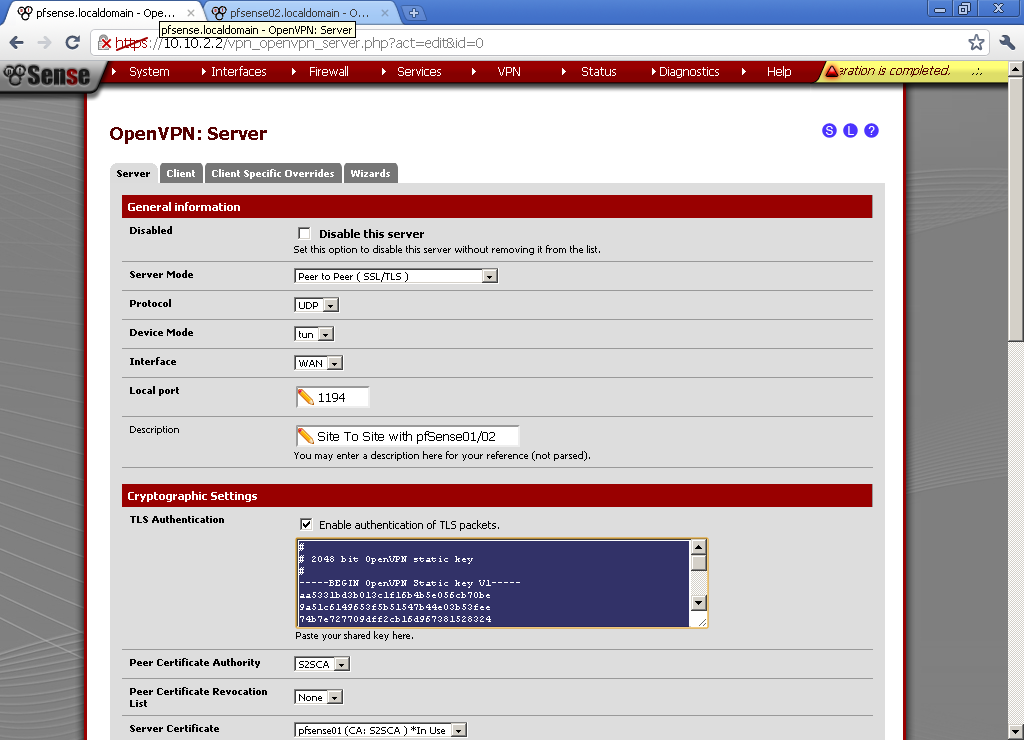
Paste it in the TLS Authentication form on our client configuration on pfsense02. Unpick Automatically generate a shared TLS authentication key and leave Enable authentication of TLS packets. 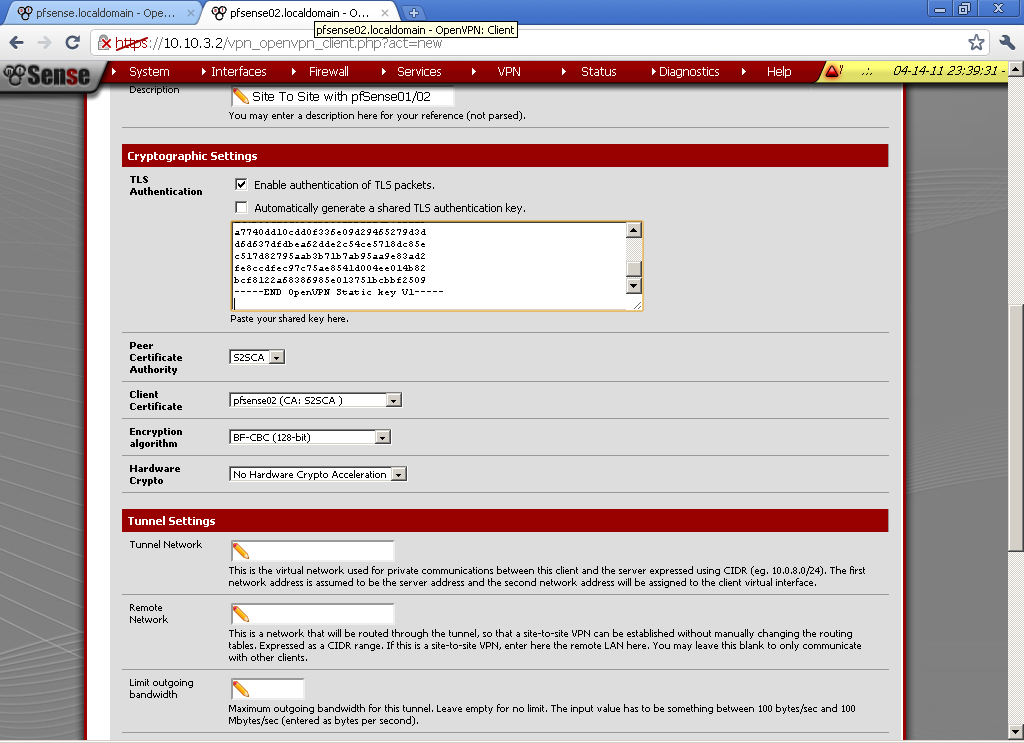
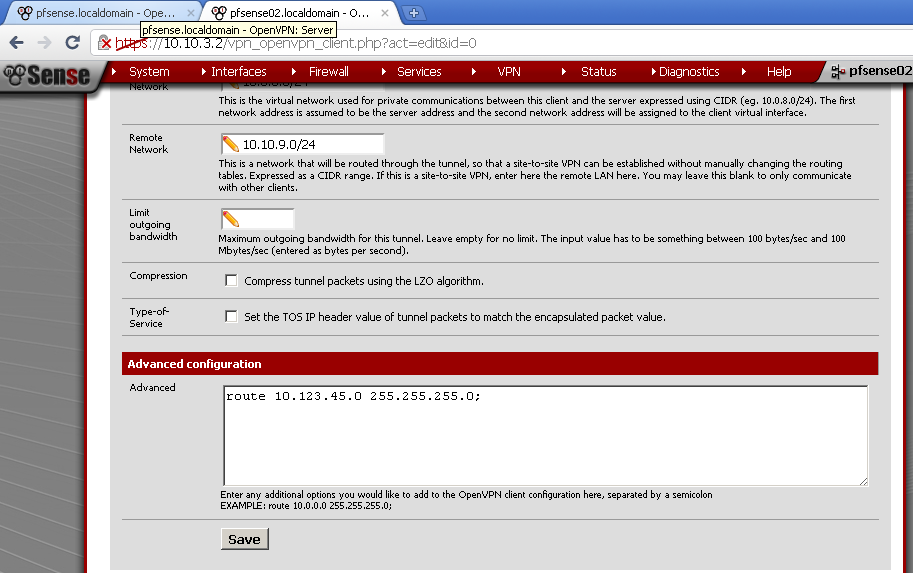
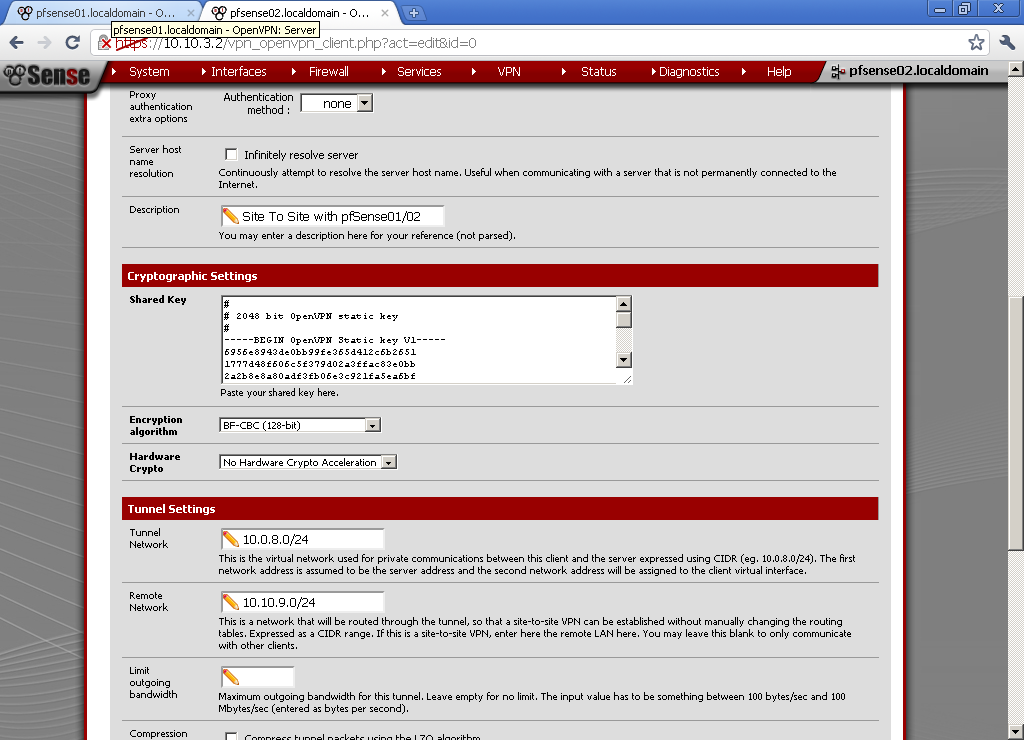
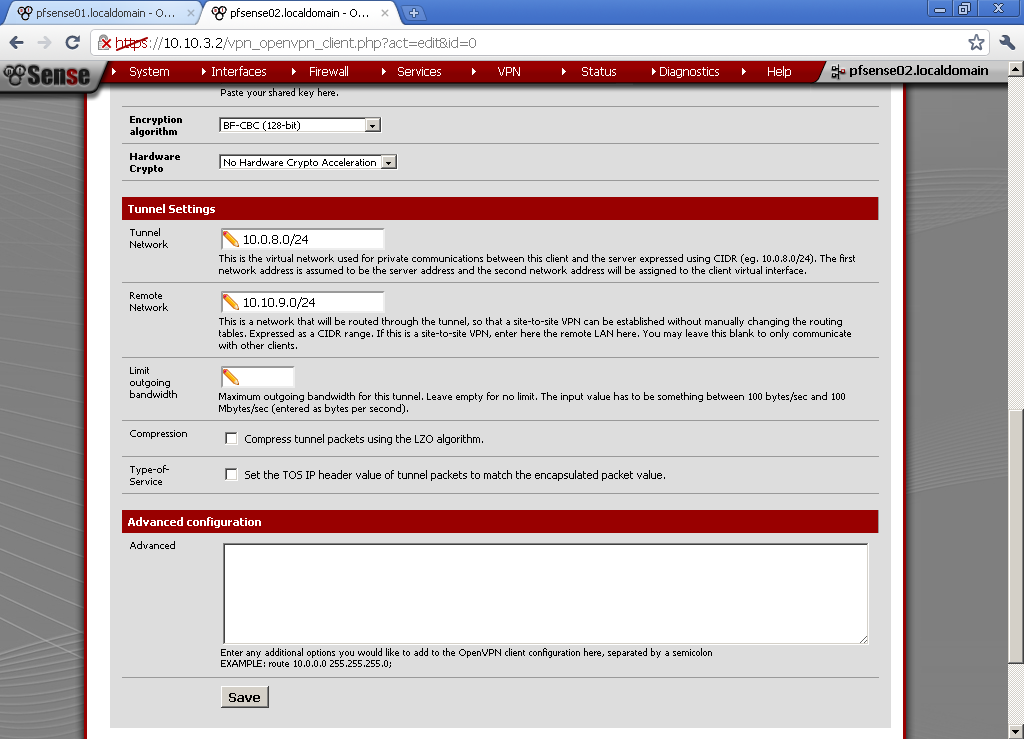
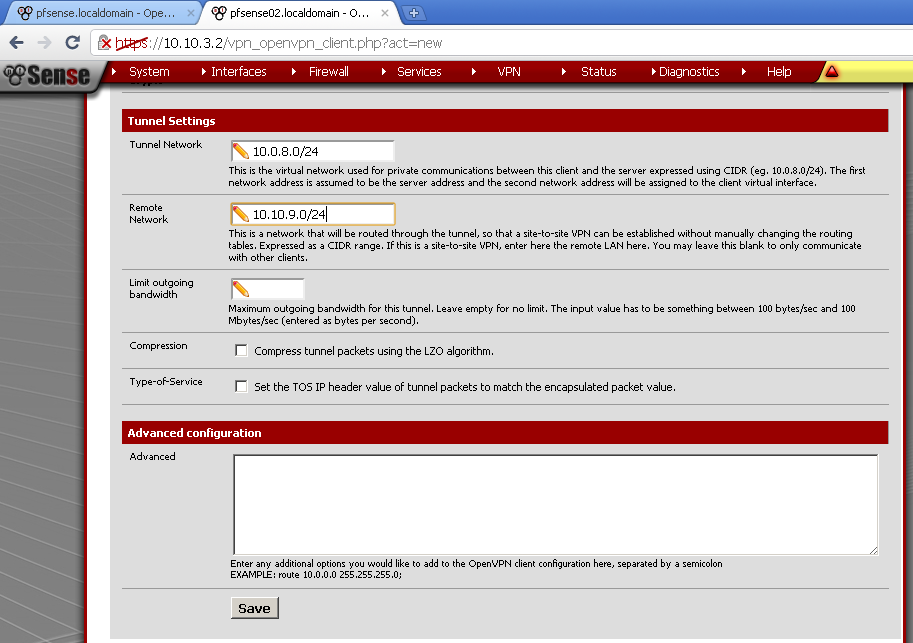
Use the same Tunnel Network as on the server, in my case 10.0.8.0/24. Enter Remote Network, this is the network behind pfsense01, for this case 10.10.9.0/24.
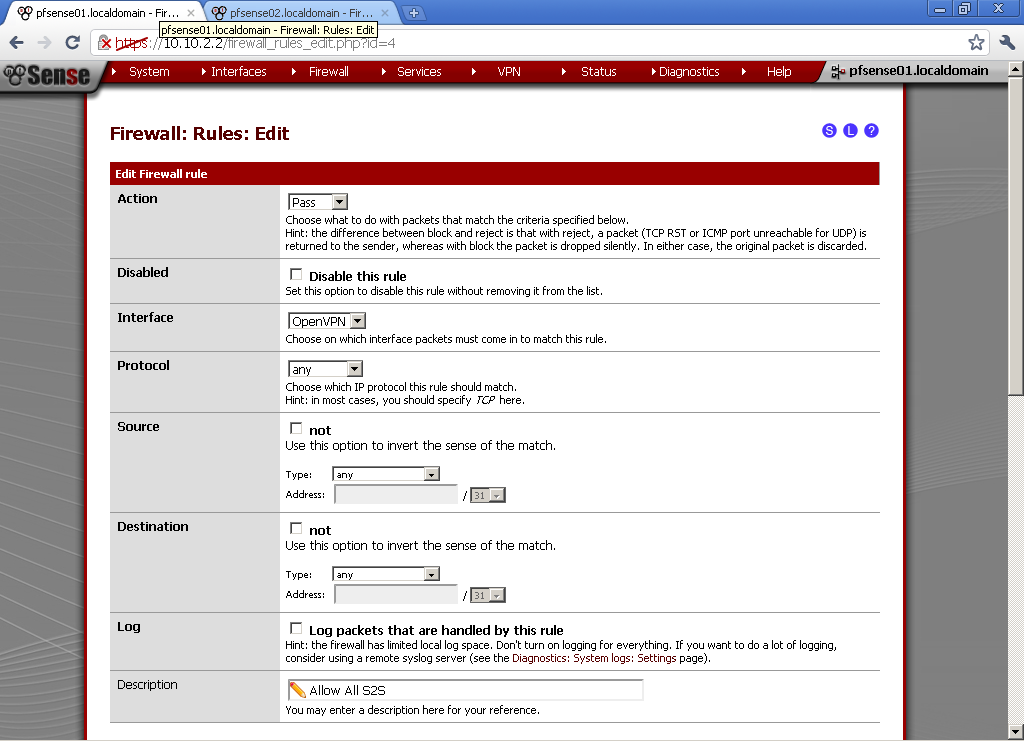
Add Allow All rule in Firewall > Rules on the OpenVPN leaf.
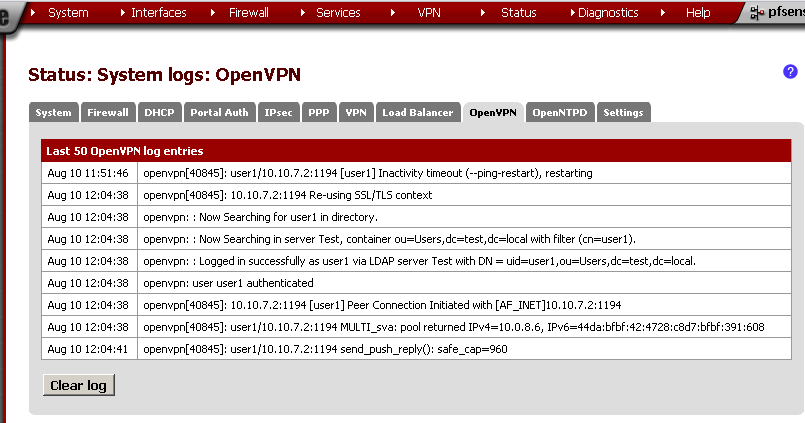
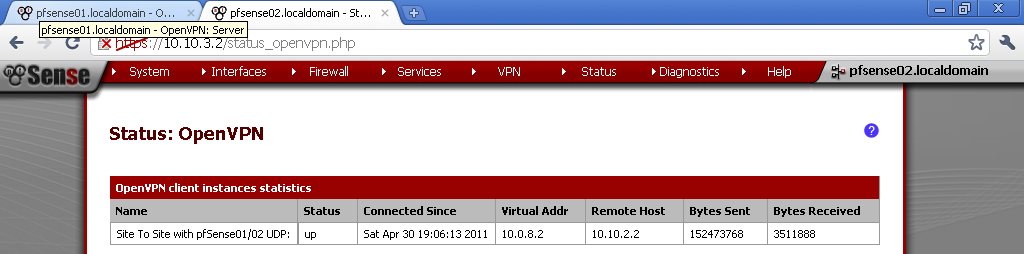
Now go to Status > OpenVPN and you should see that the connection is established.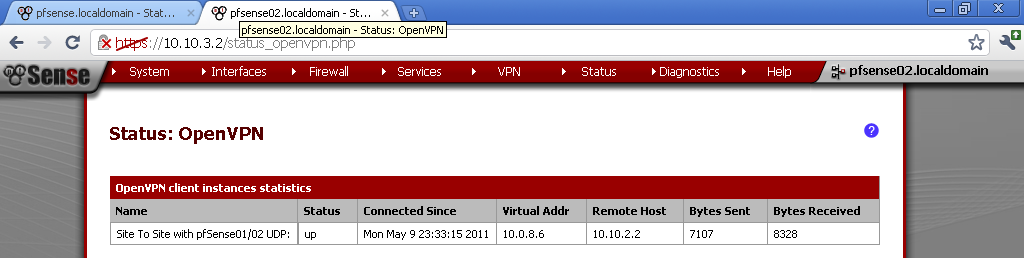
From the Server prospective, again on Status > OpenVPN.
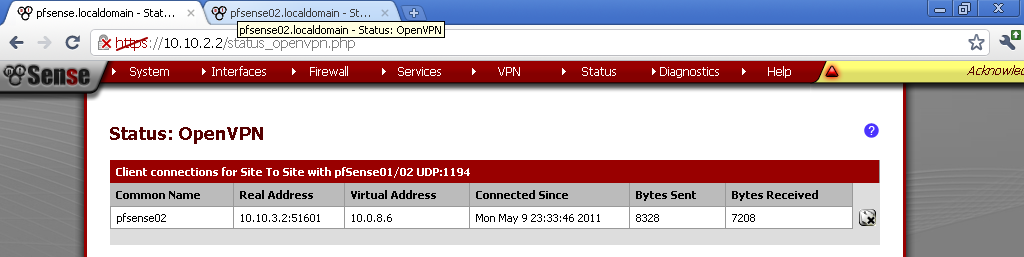
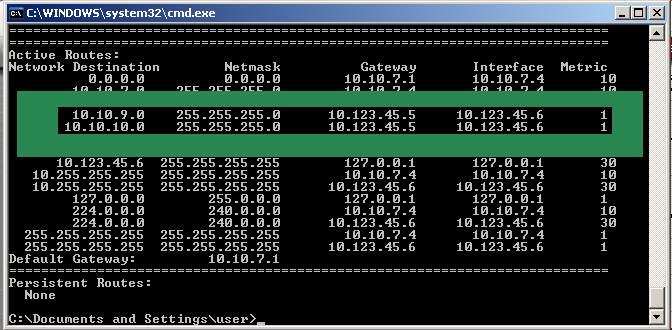
Now you should be able to access hosts from the other network successfully.