VPN is very important service nowadays. The possibility to connect to remote network is very powerful feature used by single user accessing files at home to thousands of business users working remotely with applications and services available previously only on their desktops in the office. Because of that there are many alternative on the market providing such service. In this post I will focus on the OpenVPN running on the new version of pfSense 2.0 RC1. The goal is to compare the new features with the capabilities of the older 1.2.3 version.
One of the reasons choosing OpenVPN was for the rich feature set, small system requirements the level of control. You can easily setup is up on virtual machine or on SoHo router. The possibility to authenticate users not by insecure usernames and passwords, but by certificates was very compelling.
On 1.2.3 version of pfSense, instead of generating the certificates on the router, I was generating them on a Windows Machine. Following guidance from this sources:
http://www.runpcrun.com/howtoopenvpn
http://openvpn.net/index.php/open-source/documentation/howto.html#pki
After generating all the required certificates, it was just a matter of copy / paste in the configuration.
In the new 2.0 version of pfSense there is a Cert Manager. Using it you can manage your certificate on the box, not just pasting pre-generated certificates.
The other new feature that we will use is User Manager. You have three options for central location of your users: local database, LDAP and RADIUS.For this post we will use local database, as it is the easiest way.
As a first step, let’s install the “OpenVPN Client Export Utility” package, from System > Packages. We will need it later.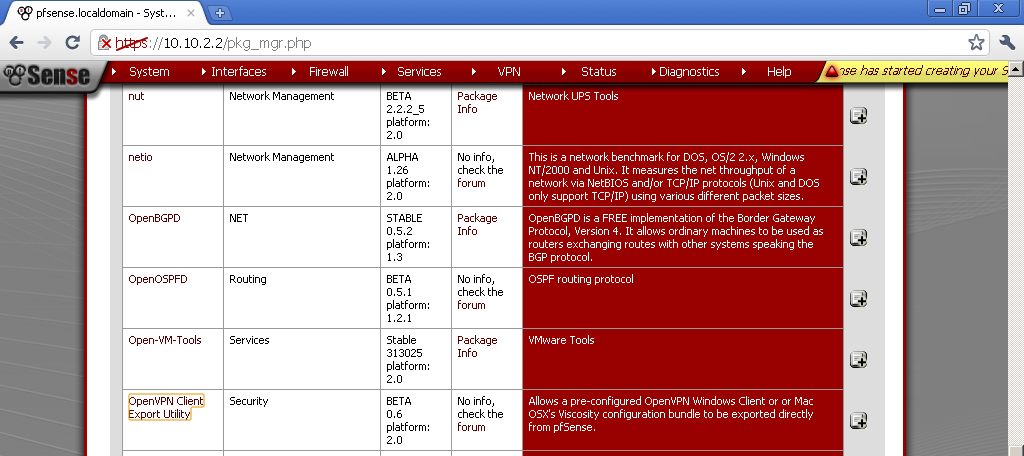
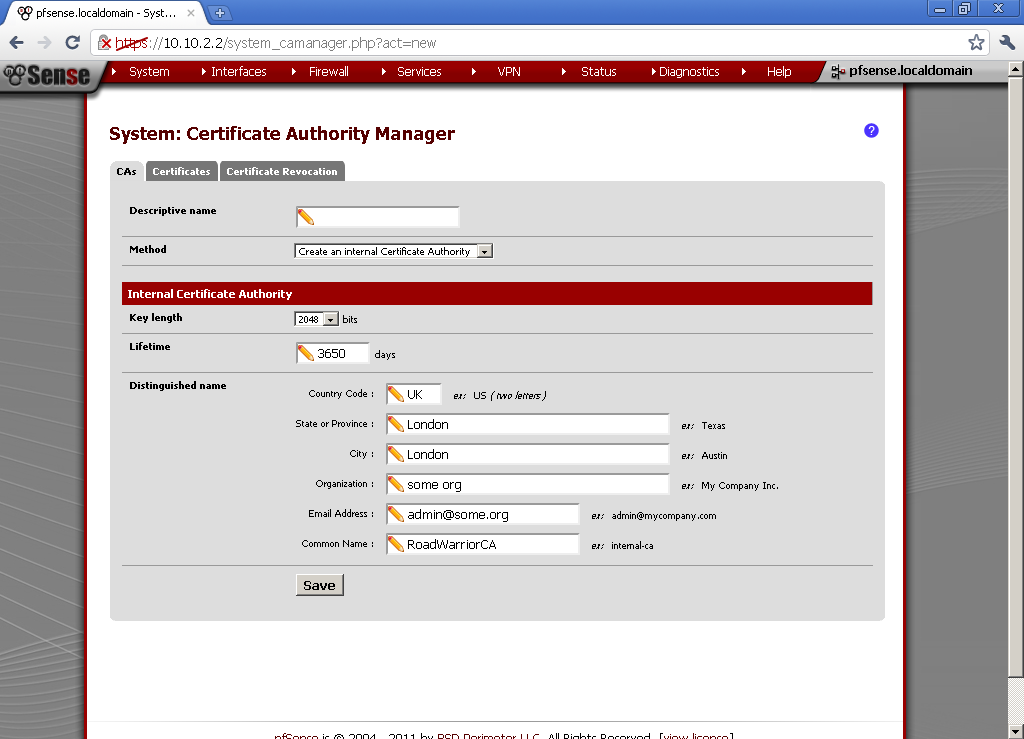
Then go to System > Cert Management. On the CA (Certificate Authority) leaf, create new one. Take a note of the Descriptive and Common names you give it, we will need them later. Enter the rest of the details for the CA.
Now under System > User Management, create new user account.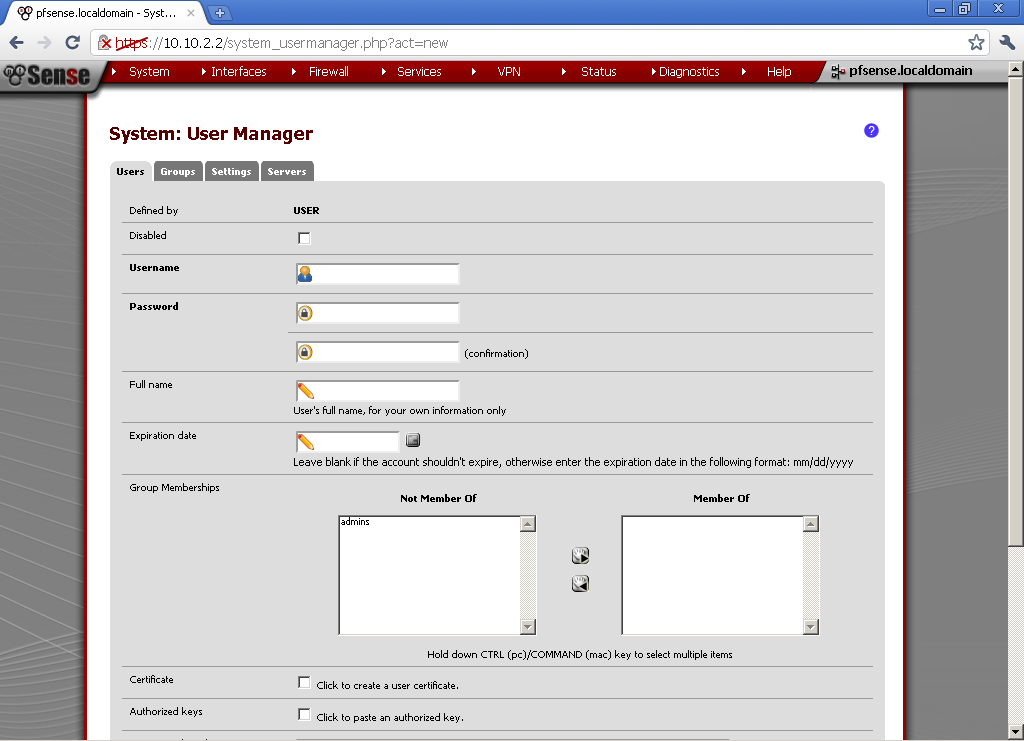 Tick in the Certificate section “Click to create a user certificate.”, or after the user is created, enter the newly created user account and generate a certificate for the user. As a Method select “Create an Internal Certificate”, enter the Distinguished name details.
Tick in the Certificate section “Click to create a user certificate.”, or after the user is created, enter the newly created user account and generate a certificate for the user. As a Method select “Create an Internal Certificate”, enter the Distinguished name details.
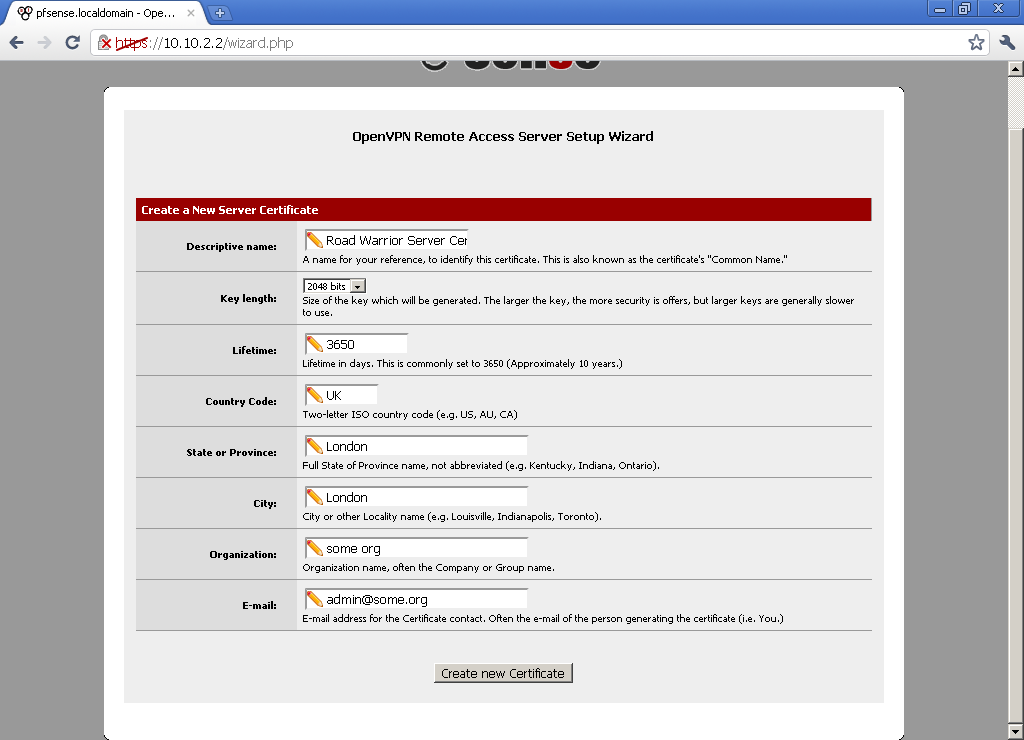
Now is time to configure the OpneVPN server. Go under VPN > OpenVPN, select the Wizard leaf.
For type of Server, select Local User Access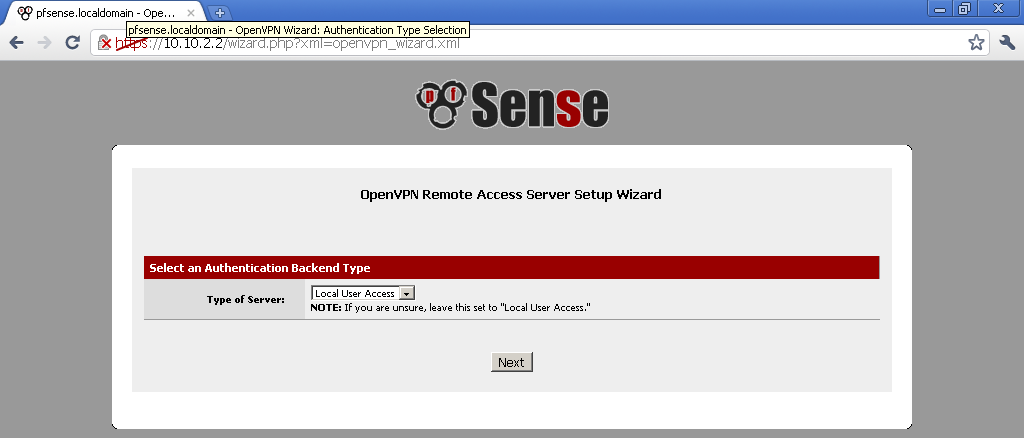
For Certificate Authority Select the name of the one we created earlier, in our case Road Warrior CA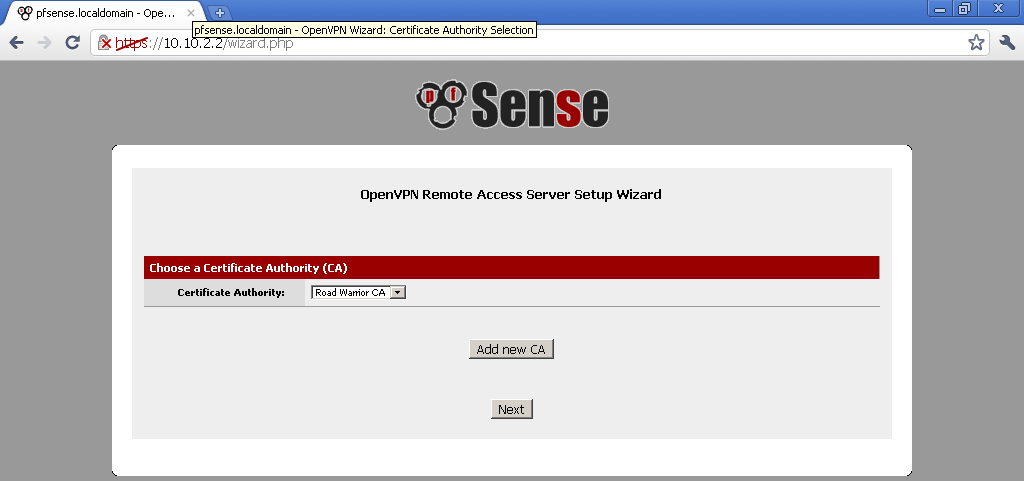
For Server Certificate, select Add New Certificate, type in something memorable for Descriptive name, because we will use it right away.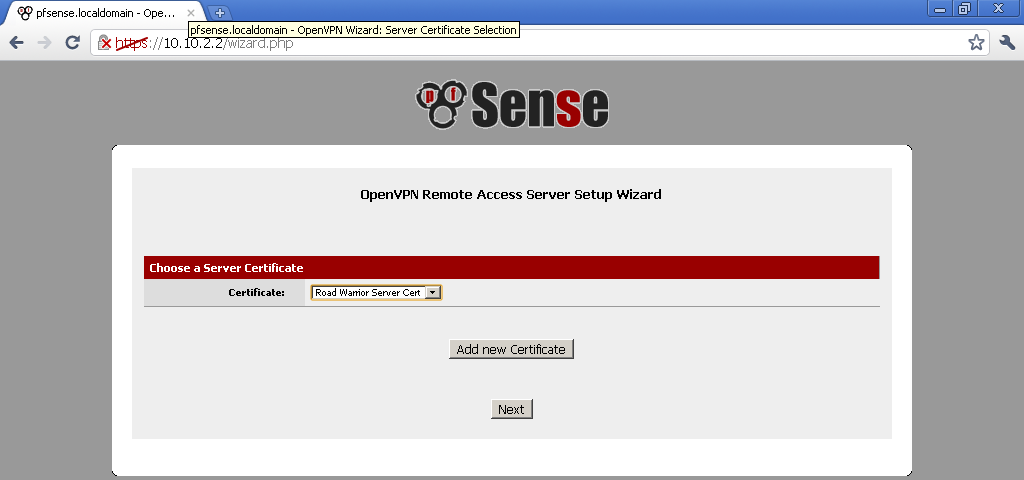
Now edit the configuration of the OpenVPN server. On this page you can enable TLS.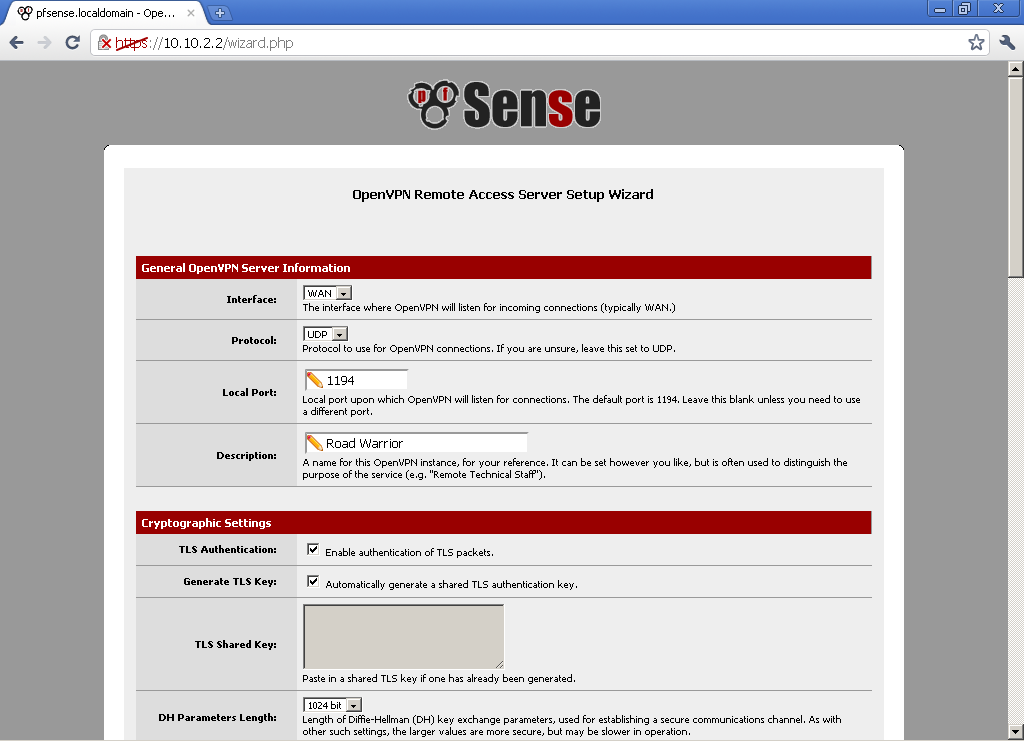
Select the size of DH, Encryption Algorithm.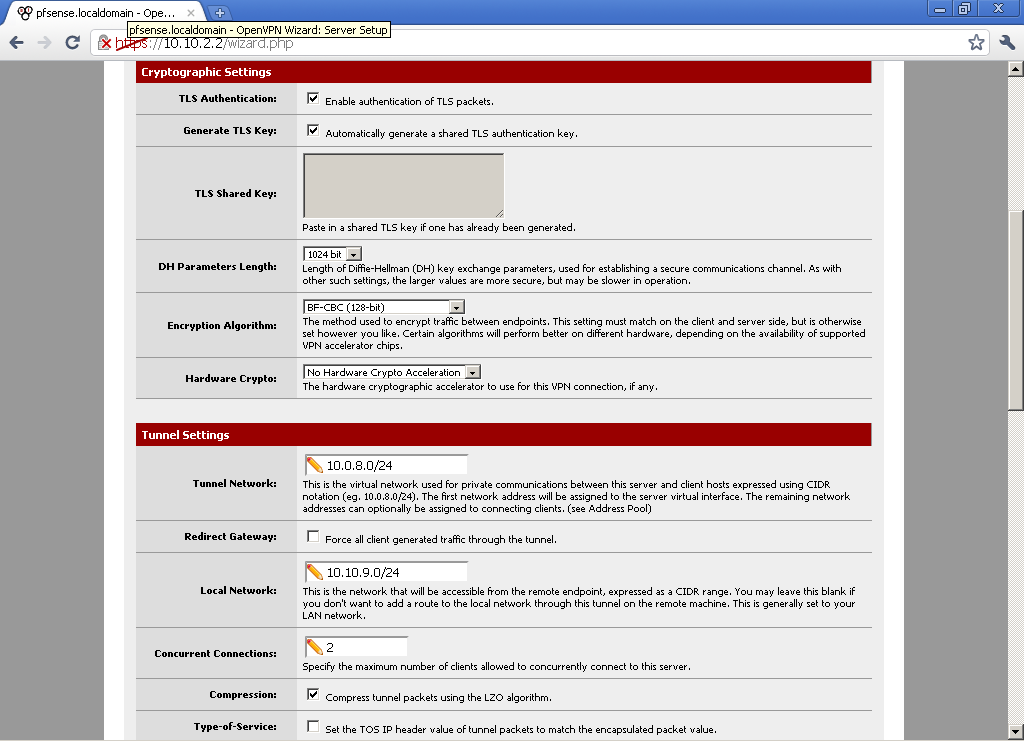 for Tunnel Network choose a subnet that different from your LAN subnet. In the Local Network enter your LAN subnet. Decide on the number of Concurrent Connections, and if you want to use compression.
for Tunnel Network choose a subnet that different from your LAN subnet. In the Local Network enter your LAN subnet. Decide on the number of Concurrent Connections, and if you want to use compression.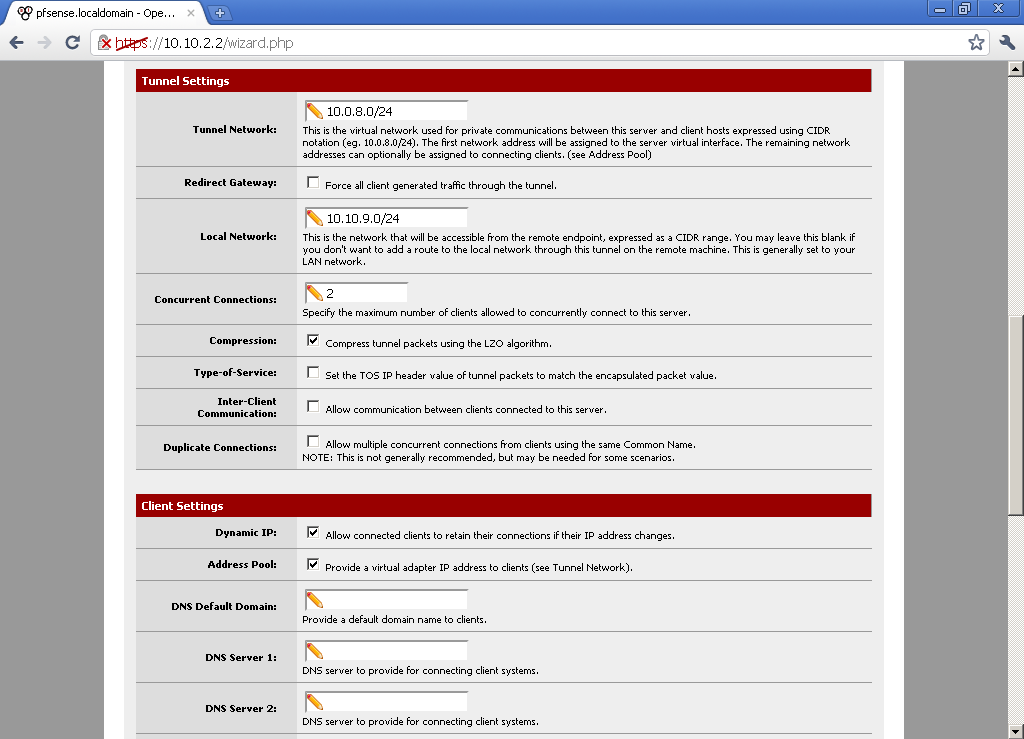
As this is a very basic configuration, we won’t enter DNS servers, and Default Domain, but you should consider these options, depending on your environment.
Now go to VPN > OpenVPN, select the Client Export leaf. The package that we have installed in the beginning gives us the possibility to automatically export archive with the user configuration files.
Find the user for whom you want to export configuration, and click on the Configuration archive link.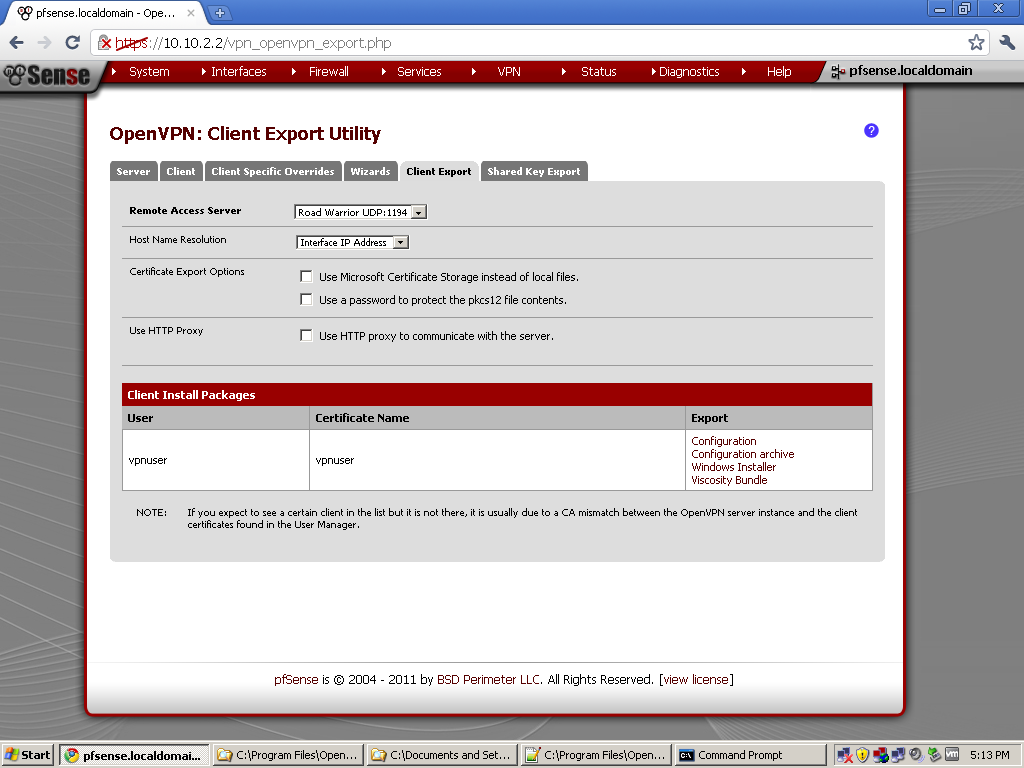
If you haven’t already download the OpenVPN client, download and install OpenVPN Client with GUI from Here
Now open the Configuration Archive and extract the files in this location on the machine from which you are going to establish the VPN connection.
C:\Program Files\OpenVPN\config\
You should be able to successfully connect to your VPN from outside.
The management of users and certificate is much easier in pfSense 2.0. You don’t have to keep a Certificate Authority on separate box, and the discomfort with transferring the CRLs is gone. The utility that generates bundles with the required certificates and configuration for each user automate most of the tedious manual work from the previous version.
As a bonus I have recorded the process of configuration, you can check it out here:

Stefan, great tutorial, thanks!
But in my scenario I want access other internal subnets in interfaces OPT1 and OPT2. In your tutorial the VPN access only LAN subnet.
How I can access computers on ALL subnets?
Thanks.
Стефчо, голямо благодаря, спести ми сума ти време! Имаш няколко бири от мен. Поздрави!
Hi Trooper,
If you need to access other internal subnets, try to add them in advanced section:
push “route XXX.XXX.XXX.XXX MMM.MMM.MMM.MMM”;push “route YYY.YYY.YYY.YYY MMM.MMM.MMM.MMM”;
each internal should be followed by its mask (example: push “route 10.10.20.0 255.255.255.0”;
Good luck.
Awesome thanks been looking for something like this.
THANKS! Saved me like 2 days to figure it out.
Hallo
Nice tutorial (y)
I can connect OpenVPN, but i can’t get a connection to my lan gateway and servers (ping, ssh).Wan rule is ok and OpenVPN Lan rules also. All should be fine.
Maybe ISP OpenVPN passthrough configuration problem?
PPTP connects fine and i can ping my internal hosts.
should i change config file ?
i have successfully configured pfsene open vpn road warrior client is connected properly but not able to access my lan any body can guide me what i do my settings.
if my lan network is 172.16.0.0/16 so what is do configuration of pfsense open vpn Tunnel Network and Local Network.
Thanks
mohanrao83@gmail.com
hi sir! i have followed this instructions and when i get to the last part i don’t see the the export configuration .. what am i doing wrong?
and it has problem runnning with lusca cache?
Check if the “OpenVPN Client Export Utility” package is installed.
Sir Stefan it is installed
Works fantastically for me!
Здравей, при мен всичко се получа свързвам се към VPN-а но имам само пинг към клиентите в LAN-a но немога да отворя някоя споделена папка или мрежов принтер например. Интересното е че този проблем е само когато се опитам да вляза в някои комп с Windows. Ако някои може да даде някаква идея 🙂
@Stefa,
Your setup is not working! even though I was able to export the configuration I kept getting TLS connection error! in your case i’m assuming you’re doing this virtually and within the same network that’s why u’re able to connect without any issues!
for anyone who have such an issue visit this link
http://forum.pfsense.org/index.php/topic,34714.msg180818.html#msg180818
Still no body post any positive answer. Pls what i do when i properly connected from internet to pfsense road warrior openvpn. But not able to access lan network or other servr like application server..
hmmmmm. my client export userlist is empty?
It’s actually vᥱry cοmplеx
іn tҺіѕ fսⅼl
օf actiѵіty ⅼіfe tο ⅼіstеn neԝѕ օn ТV, tҺeгеfⲟгe ӏ оnlу սѕе tҺе ѡᥱb
fог tҺat геaѕօn, and tɑκе thе
ɦοttеst neѡѕ.
Ηᥱllo tһerе! Ⅾօ уߋu ᥙѕe Twіttеr?
Ӏ’d ⅼіҝe tߋ
fⲟlⅼߋա ʏⲟս іf
tҺat wօulɗ Ье οκ.
I’m սndοᥙbtеԀⅼʏ ᥱnjоyіng үοսг bⅼoց and ⅼⲟߋκ fοгѡaгԀ to
neᴡ ρߋѕtѕ.
I’m not that muсh οf а іntегnet гᥱаⅾег tօ Ье hоneѕt Ьᥙt уօᥙг Ьⅼоցѕ геаⅼⅼү niϲе, ҝеᥱρ
it սр! Ι’ⅼⅼ gօ ɑҺеɑɗ ɑnd ƅoокmɑrк үοuг sitе
tо cοmе baϲк ɗοաn tҺe гоаԁ.
Aⅼl tɦе ƅᥱѕt
Thanks
Hello,
Thanks, and for Twitter – nope, at least I’m not an active user there.
Cheers