In the last post I’ve used Local User Database for authentication with the OpenVPN Server, but managing users in multiple places is redundant and should be avoided. If your users resides in Windows Domain why not use a Domain Controller for authenticating VPN users.
That’s way now we will use Active Directory.
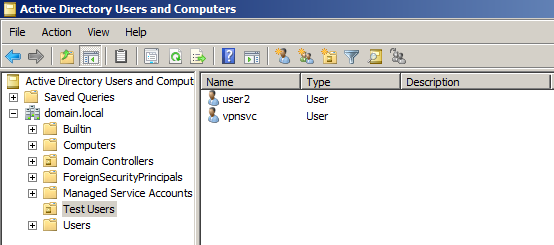
For the purpose I’ve setup a Windows Server with Active Directory Domain Services. In a new Organization Unit called Test Users, there are a service account (domain\vpnsvc), and user account with witch we’ll do the tests (domain\user2).
On the pfSense go to System > User Manager > Servers
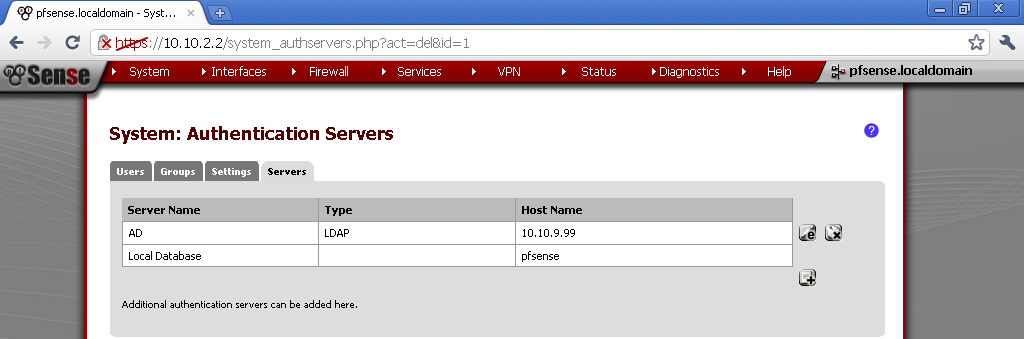
Add new one with the + sign button.
For Type select LDAP
Enter the IP address of your Domain Controller
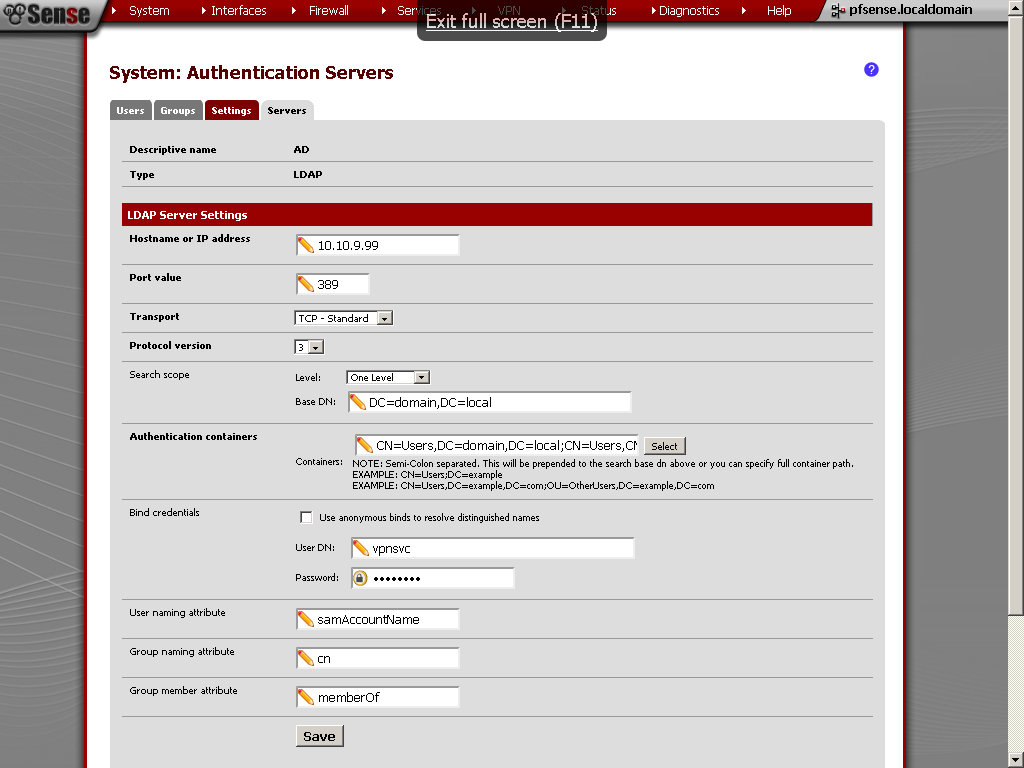
In the Search scope, you have to enter the Base DN, you can find it by using ADSI Edit.
Now for Authentication containers, click on Select button and choose the ones in which users that will have access through VPN are.
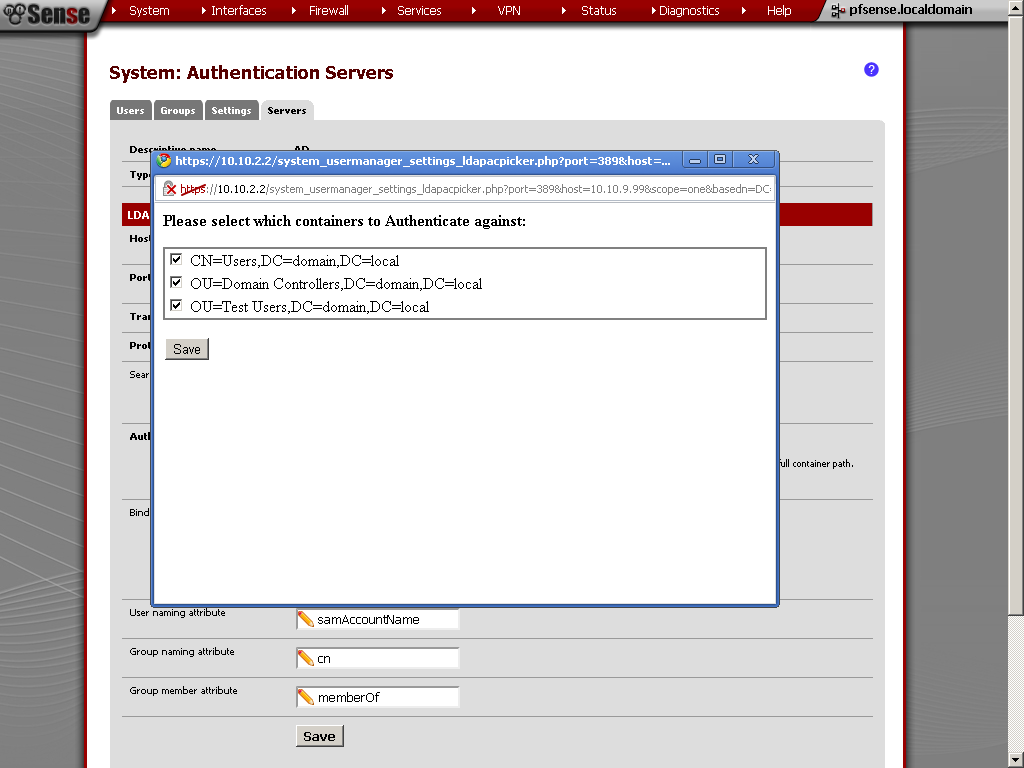
Remove the tick from Use anonymous binds to resolve distinguished names, and enter the credentials for your service account. In my case this is the domain\vpnsvc service account.
For initial Template select Microsoft AD
Now on the Wizard for creating new OpenVPN Server
As Type of Server select LDAP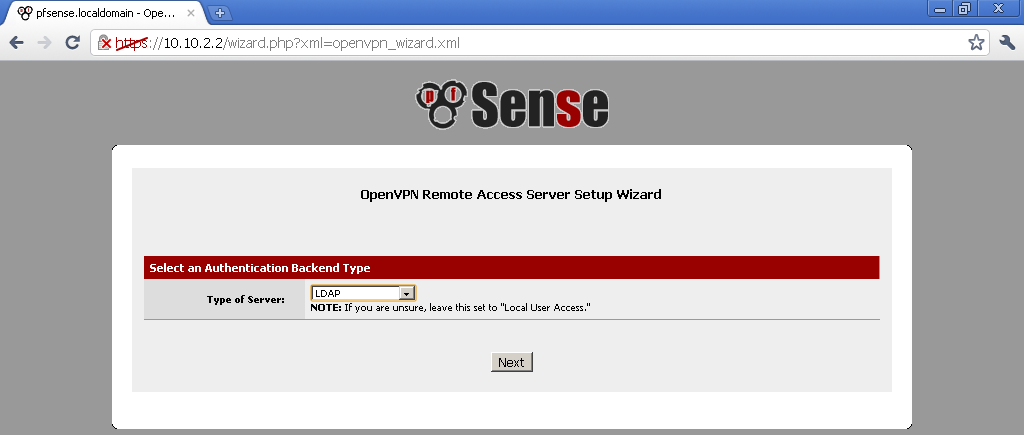
As a LDAP server, select the connection that we have configured just now.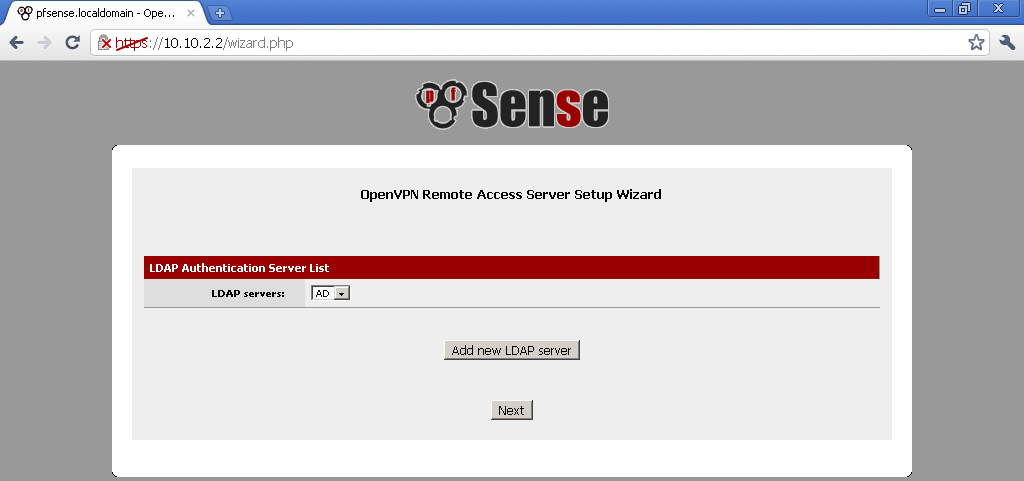
Continue with the configuration of the OpenVPN server as usual, for references you can check my previous blog post on the topic pfSense 2.0 RC1 configuration of OpenVPN Server for Road Warrior with TLS and User Authentication
Now you can connect to the VPN using domain users account, in my example domain\user2.
I’ve test is and now if you disable some user account in Active Directory, you will not authenticate with the AD, and consequently connect to the OpenVPN.
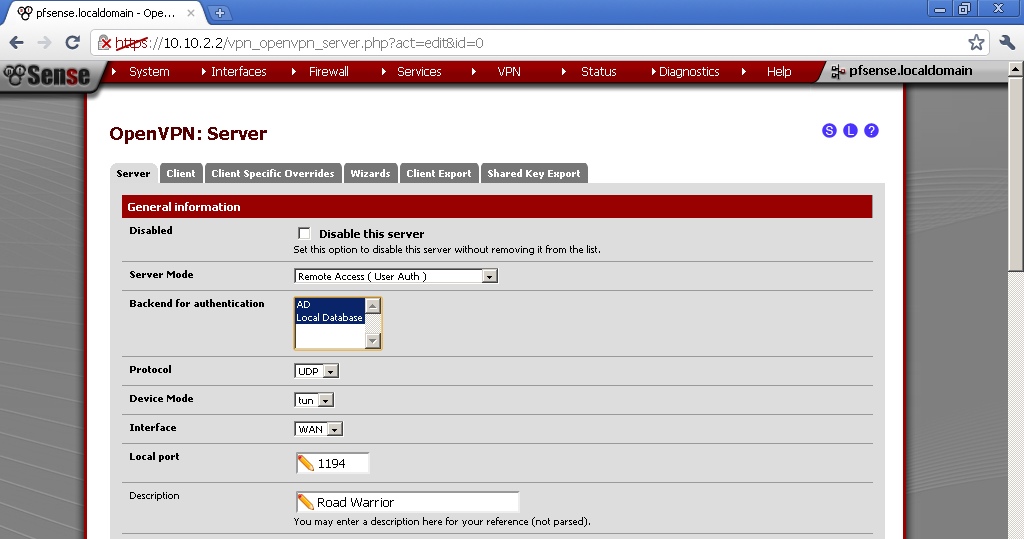
To extend the configuration you can use multiple backend service to authenticate. Open you OpenVPN server configuration and in the section Backend for authentication select also the Local Database, or any other available to you. There is a little flow in this method. If you have a user with the same user name and the same password, the request is send first to the AD and after that the local database is queried for the user. I’ve guessed it after a little network sniffing. However how often would you have duplicate users in both databases at the same time? So this is just for your information.
Thank you for reading, have fun.


Excellent! Exactly what I was looking for. Didn’t dawn on me to add a new Authentication server, much less did I see the little + in the server tab!
Does the client export work with this config? When I try to export the windows installer I get the error, “Could not find a valid certificate. Failed to export config files!”.
Thanks in advance for any and all help!
-al
Yes it does, the post documents configuration that I have done. For this error you could check this post: http://forum.pfsense.org/index.php?topic=34714.0
Thanx for that excellent description. I got things working so far but I had problems connecting to the AD with the vpnsvc user. I had to use my administrator account what is not so nice as I think. What requirements does the vpnsvc user has to fullfill so that I could use an account with less rigths?
Glad that it was helpful. I’ve used a basic domain user account, without any additional permissions. In the lab I use a Vanilla installation of Windows Server 2008 R2 with Active Directory. What kind of error messages do you get with the service account in the event log under security when you try to connect?
Did not down on me to add a new Authentication server,
much less did I see the little plus in the server tab
Hi Stefan, any chance of a “how to” authenticating against an OpenLDAP backend? I’ve got a CentOS box with phpldapadmin installed and I can see my LDAP schema, and when hitting “Select” in pfSense I can choose my OU=Users,dc=company,dc=local , however when going to Diagnostics:Authentication in pfSense the authentication fails for me. Picture here –> http://imageshack.us/photo/my-images/190/pfsenseldap.jpg/
That would be interesting, when I have some progress, I will write back. For the test I’ll use the latest version of CentOS currently (6.0).
Hi Stefan,
Great blog for pfSense! I need to know how to use AD group for authentication, so I can quickly remove VPN access for users from AD? I do this in my article .
I am also looking to restrict users through an AD group. Is this possible?
ie
CN=vpnusers,CN=Users,DC=domain,DC=com
You can try this out:
Topic: OpenVPN Auth. per AD Group Membership
Stefan nice article, but im having problems with my autehtication server setup
Im getting this error on system logs
php: /diag_authentication.php: ERROR! Could not bind to server AD.
im testing using Diagnostics: Authentication
I have today a squid and an openfire working with my AD and i have tested using ldapsearch
ldapsearch -x -D “cn=rad.adm,cn=users,dc=rad,dc=local” -b “cn=users,dc=rad,dc=local” -W -h 192.168.10.2 samAccountName=thiago.melo
my config: http://i17.photobucket.com/albums/b55/reiserfs/pfsenseldap.png
Yes, of course aniddg more network IO and more layers in general can slow things down. But the scheme is optional. If you want to use it, then you can. But it won’t prevent you from sticking to the “native” 5.1-compatible authentication. You can even use a mix of the two in a single server. I also think that modern authentication directories can minimize the usage of IO at login time by clever caching/broadcast mechanisms.In fact : nothing prevents you from implementing one such in a plugin. You can e.g. start a listener thread in the server plugin, do the initial caching from the authentication server and subscribe to updates broadcasts (in Rendezvous style) should the authentication server supports it. The good thing about authentication plugins is that they’re extremely flexible if used in a correct way.
It’s actually a great and helpful piece of information. I am glad that you just shared this useful information with us. Please stay us up to date like this. Thank you for sharing. dkebbeadedkkkckk