Sometimes you need to map internal machine IP to real IP address accessible from the Internet.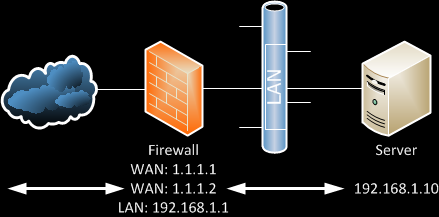 As on the diagram if someone makes a request to 1.1.1.2, the request is send to 192.168.1.10.
As on the diagram if someone makes a request to 1.1.1.2, the request is send to 192.168.1.10.
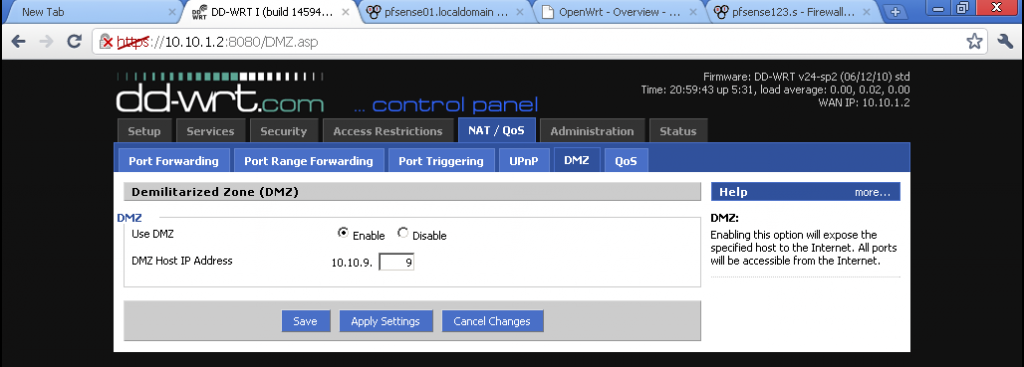
On DD-WRT you can use DMZ. This service is pseudo-DMZ, more commonly known outside of the SoHo routes as Exposed host.
To set is up enter the NAT / QoS section, then select the DMZ subsection, and configure your internal IP. For more information read here
Be warned that exposing all port of a machine to the Internet is very insecure, and even worse if the machine does not have some kind of firewall.
In pfSense, the alternative is to use VIP and 1:1 NAT
You can’t do that in 1.2.3, if you have only one WAN IP, if you do an error message appears: “The WAN IP address may not be used in a 1:1 rule”. Alternative is to make a port forward, which is much more preferable especially if not all ports are included.
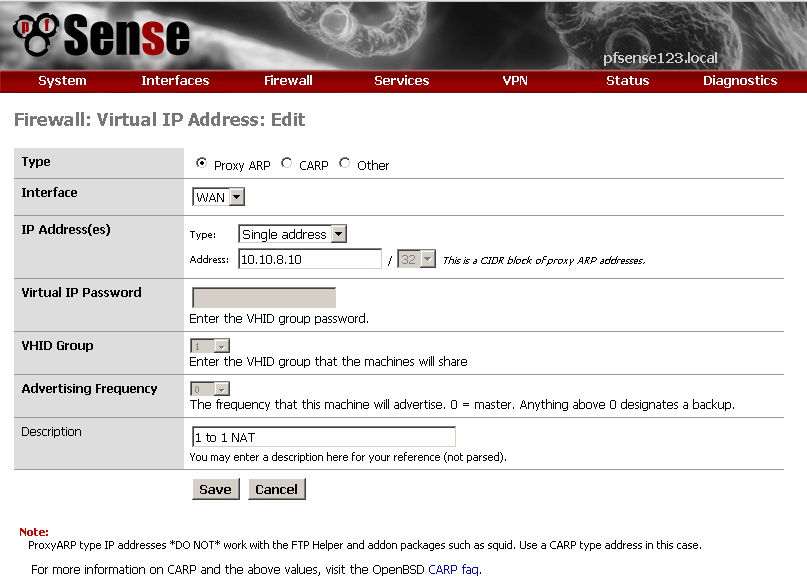
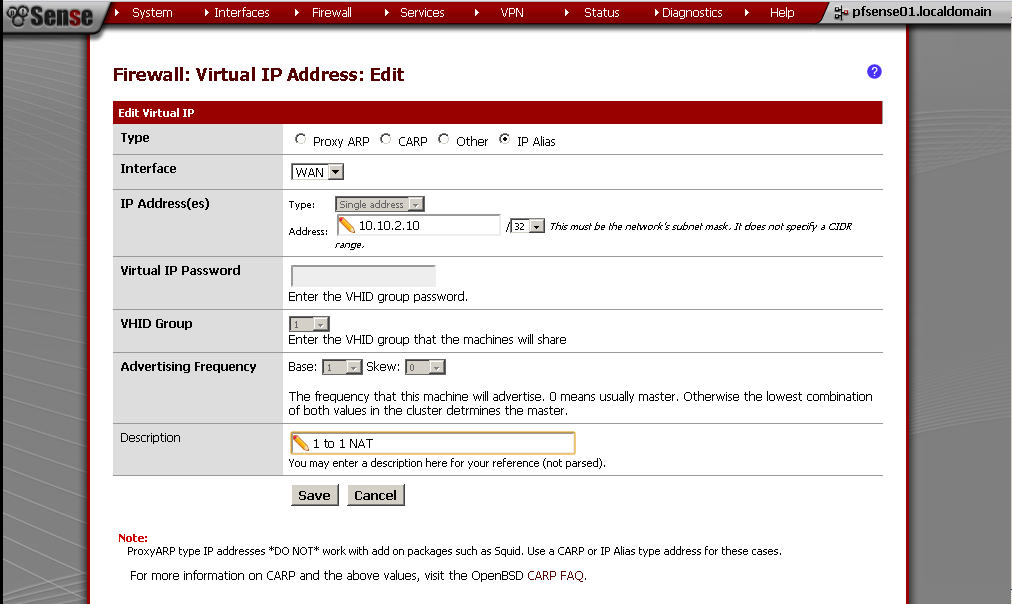
So first you must add your additional WAN IP in the Virtual IP section.
For Type you can choose between Proxy ARP and CARP, detailed explanation why check out here
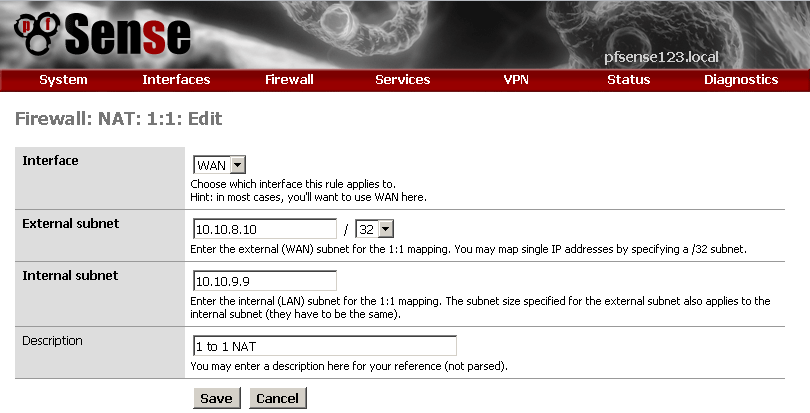
Then create a 1 : 1 NAT rule
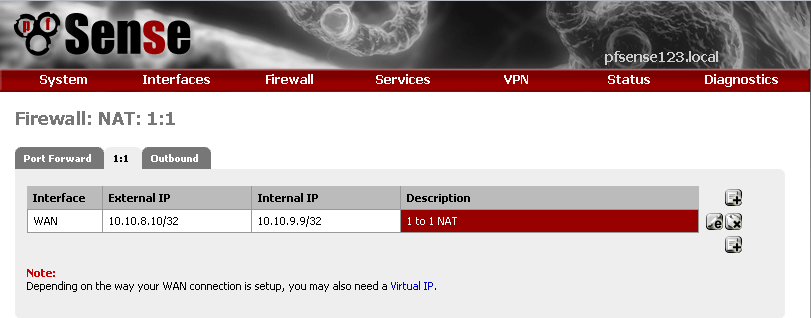 Nothing special in the configuration, just enter your internal and external IPs and description for the rule.
Nothing special in the configuration, just enter your internal and external IPs and description for the rule.
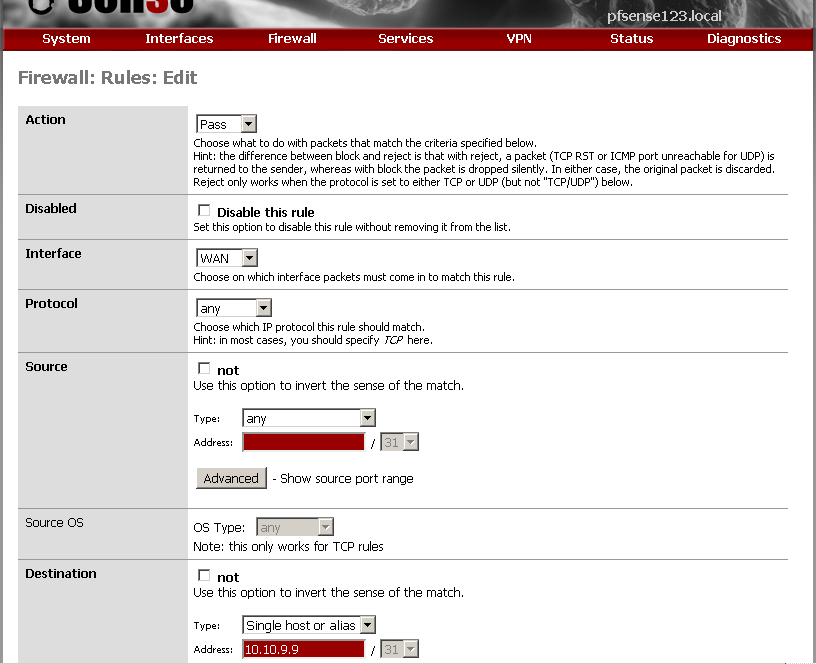
You must make a firewall rule for all this to work, enter the internal LAN IP address as destination.
On pfSense 2.0 RC1, except the huge amount of new options the only difference is the new option in the Virtual IP type selection. The IP Alias works fine in this setup. The other good news is that even if you have only one WAN IP address you can use is in such setup. The bad news is that you do use it you can’t use your WAN IP for anything else, all port on the WAN IP are mapped to the machine on the LAN.
Alright so far this was the case if you have need to publish only one IP, but if you need to do this for multiple machine and have more than one WAN IP address, the procedure is a little different.
On pfSense you just repeat the procedure as many times as you need.
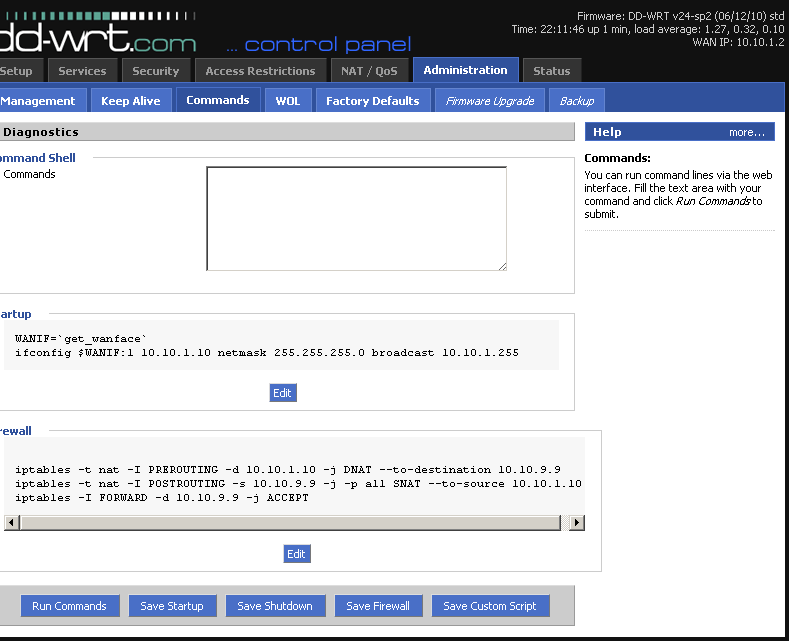
On DD-WRT you can add some iptables rules.
Add these lines to the Startup script:
WANIF=`get_wanface`
ifconfig $WANIF:1 10.10.1.10 netmask 255.255.255.0 broadcast 10.10.1.255
This adds the new WAN Ip to the Interface
Add these lines to the Firewall script:
iptables -t nat -I PREROUTING -d 10.10.1.10 -j DNAT –to-destination 10.10.9.9
iptables -t nat -I POSTROUTING -s 10.10.9.9 -j -p all SNAT –to-source 10.10.1.10
iptables -I FORWARD -d 10.10.9.9 -p all –dport all -j ACCEPT
10.10.1.10 – this is the WAN IP address
10.10.9.9 – this is the LAN IP address
Add these lines for as many IP as you have / need. More on the topic here.
In conclusion, this is a very quick and dirty way to publish internal machine to the internet, bear in mind that this host is fully exposed to anybody on the Internet. I personally don’t recommend this way of publishing, but if need arise you can consider this an option. In future posts I will try to present more smart and safe ways to publish some service.

1:1 nat for 2.0RC1 do not work!
Hi, yes it does, did you reboot the pfSense after you configured it?
I’ve just verified it in my lab. After reboot is it OK.
Regards
Really interesting articles. I enjoyed reading it.